Security researchers have uncovered a Facebook malvertising campaign spreading Brokewell spyware to Android devices. The campaign uses fake TradingView ads to lure victims into downloading a trojanized app, which then steals cryptocurrency wallet details, personal data, and other sensitive information.
How the Malware Works
According to researchers, attackers cloned TradingView branding to distribute a malicious APK hosted outside the official Google Play Store. When victims clicked the fake Facebook ad, they were redirected to a fraudulent landing page that closely resembled TradingView’s legitimate site.
Once installed, the Brokewell spyware embedded itself deeply into the device. It harvested keystrokes, intercepted SMS messages, stole saved credentials, and scraped data from crypto wallet apps and banking platforms. The spyware also granted attackers remote access, allowing them to issue commands and exfiltrate data in real time.
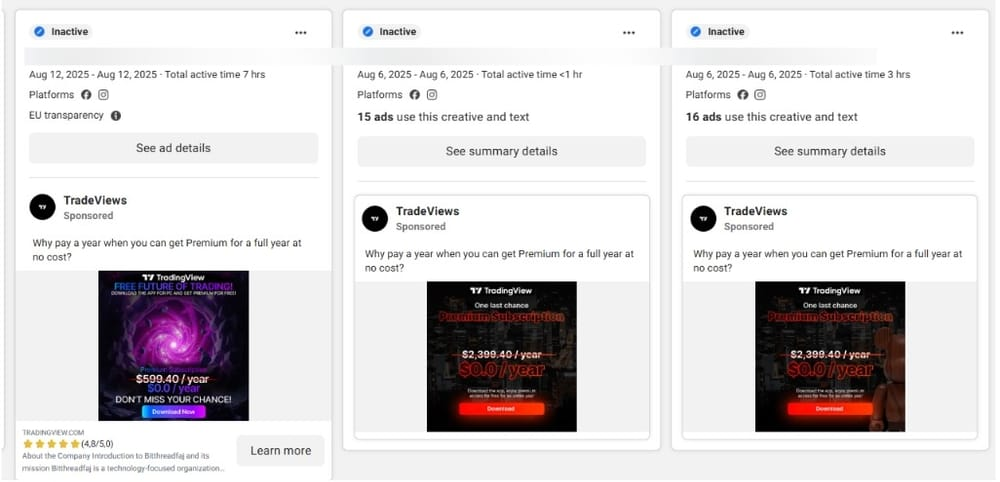
Malicious Ads That Spread BrokeWell Malware (Source: BitDefender)
Why Android Users Are Targeted
Android’s open ecosystem makes it more vulnerable to malware campaigns distributed through unofficial app stores or sideloaded APKs. By exploiting Facebook’s ad platform, attackers reached a wide pool of potential victims quickly, bypassing Google Play’s built-in protections.
Researchers noted that this particular campaign targeted cryptocurrency traders, who often rely on TradingView charts for market analysis. By hijacking that trust, attackers maximized their chances of compromising high-value accounts.
The Brokewell Malware Family
Brokewell is not a new threat. It has appeared in multiple Android malware campaigns over the past two years, often tied to financial theft and credential harvesting. The latest campaign, however, represents a more refined approach by leveraging social media ads to seed infections.
Security experts believe the group behind Brokewell is improving distribution tactics, shifting from traditional phishing SMS (“smishing”) to ad-based delivery on trusted platforms. This strategy blurs the line between legitimate promotions and malware delivery.
Facebook and TradingView Responses
Neither Facebook nor TradingView has issued a public statement yet, though Facebook has confirmed it is investigating malicious ad reports. TradingView clarified that it does not distribute APK files and urged users to only download apps from official app stores.
Security researchers have reported the malicious domains and said takedown efforts are underway. However, new landing pages may reappear as attackers adapt.
Protecting Against Android Malware
Experts recommend the following steps to reduce risk:
- Only install apps from Google Play Store or trusted vendors.
- Avoid clicking app download links from ads or messages.
- Use mobile security solutions that detect spyware and trojans.
- Regularly audit app permissions and revoke unnecessary access.
- Enable Google Play Protect and update Android devices frequently.
The Brokewell spyware campaign underscores how easily malvertising can exploit trusted platforms to spread Android malware. By targeting crypto traders through fake TradingView ads, attackers combined financial theft with mass distribution, putting both individuals and businesses at risk.
Researchers warn that social media platforms will likely see more malvertising-driven malware in the future, making user awareness and mobile defenses critical.





