Security analysts from JFrog have identified eight malicious NPM packages designed to steal sensitive information from Google Chrome users on Windows systems. The discovery highlights a growing risk in the software supply chain, where attackers weaponize widely used developer tools to target unsuspecting users.
How the Attack Worked
JFrog researchers revealed that the rogue NPM packages contained over 70 layers of obfuscation to evade detection. Once installed, the packages executed hidden scripts that searched for Chrome browser data on Windows endpoints.
The malware exfiltrated:
- Stored passwords from Chrome’s credential vault
- Session cookies
- Autofill data, including saved emails and addresses
- Potential authentication tokens linked to web apps
Packages uploaded to the npm repository (Source: jfrog.com)
Attackers then sent the stolen information to command-and-control (C2) servers under their control. By focusing on Chrome, the world’s most popular browser, the campaign maximized its impact on both developers and end users.
Why NPM Was Targeted
NPM (Node Package Manager) remains the backbone of modern JavaScript development. With millions of packages downloaded daily, it is a prime target for adversaries conducting supply chain attacks.
Unlike direct phishing campaigns, malicious packages inserted into NPM can spread silently across projects, infecting multiple downstream applications. Developers who unknowingly installed these trojanized packages on Windows machines inadvertently exposed sensitive Chrome data.
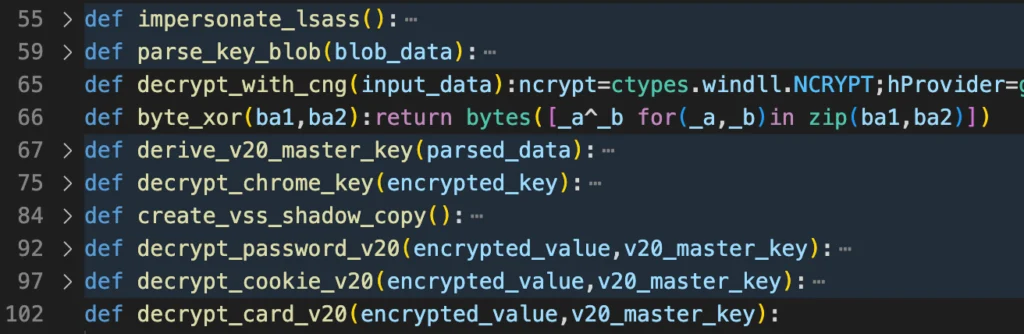
Screenshot from the final payload with function declaration of the malware capabilities(Source: jfrog.com)
Obfuscation as a Defense Evasion
The use of 70 obfuscation layers demonstrates the lengths attackers will go to hide malicious payloads. Researchers said the code was intentionally nested and fragmented, forcing analysts to peel back layer after layer before uncovering the spyware functionality.
This level of complexity not only delays detection but also suggests a well-funded and determined threat actor. The attack fits into a broader pattern of supply chain compromises where attackers aim to infiltrate developer ecosystems instead of targeting individuals directly.
Impact on Developers and Enterprises
While JFrog did not disclose exact download counts, even a handful of developers installing the packages could have wide-reaching consequences. Stolen Chrome data may provide attackers with access to:
- Source code repositories tied to developer accounts
- Enterprise authentication portals
- SaaS tools linked through browser sessions
- Financial accounts managed via Chrome autofill or stored credentials
Such access enables further exploitation, including source code theft, corporate espionage, and identity fraud.
This incident shows how attackers increasingly leverage supply chain attacks to compromise trusted developer ecosystems. By embedding spyware in NPM packages and targeting Google Chrome data on Windows, adversaries exploited one of the most widely used browsers and ecosystems in a single campaign.
The discovery also reinforces concerns that malicious packages are becoming harder to detect. As attackers refine their obfuscation techniques, enterprises must treat dependency management as a frontline security issue.
The malicious NPM package campaign is part of a larger trend of targeting developers as an entry point into organizations. Similar attacks have compromised PyPI, RubyGems, and other repositories. With the rise of AI-driven development tools and increased reliance on third-party libraries, supply chain attacks are only expected to escalate.
JFrog researchers concluded that protecting developers requires more than endpoint security. Organizations must integrate package vetting, continuous monitoring, and strict code auditing into their workflows to stay ahead of these threats.





