Darktrace has reported new malware hijacking Windows Character Map to conduct cryptomining attacks, exposing how everyday processes can be weaponized for hidden exploitation. The attack, detected in July 2025, underscores the growing sophistication of cryptojacking campaigns and the risks they pose to enterprise environments.
How the Attack Worked
On July 22, 2025, Darktrace’s security team detected abnormal activity within the network of a retail and e-commerce customer. The investigation revealed that malware had compromised the Windows Character Map utility, a benign system process, and repurposed it for cryptomining operations.
By hijacking a trusted process, the malware avoided raising immediate red flags in endpoint monitoring tools. Once active, it diverted the system’s CPU resources to mine cryptocurrency for the attacker.
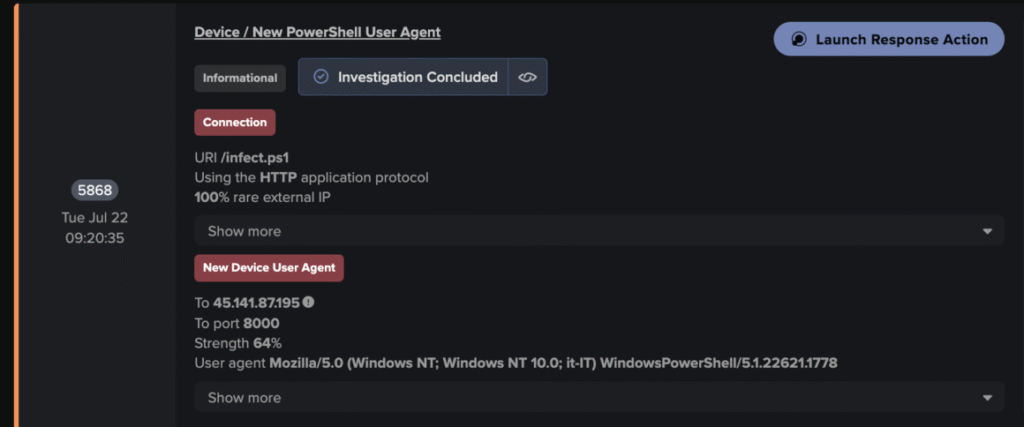
Darktrace’s detection of a device making an HTTP connection (Source: Darktrace)
The Impact of Cryptojacking
Cryptojacking is a growing cybercrime trend where attackers exploit victim devices to run unauthorized mining operations. Unlike ransomware, which announces itself, cryptojacking thrives on stealth. Victims often only notice secondary effects such as:
- Reduced system performance
- Overheating or higher fan usage
- Increased electricity costs
- Shortened hardware lifespan
In enterprise environments, cryptojacking can also degrade network performance and impact business-critical applications, amplifying the damage.
Why Windows Character Map Was Targeted
The choice of Windows Character Map (charmap.exe) highlights the trend of abusing low-profile, trusted processes. Attackers know that many antivirus or EDR tools treat system utilities as safe, creating blind spots for malicious activity.
By blending malicious operations into a familiar Windows process, the malware significantly reduced its chances of detection. Darktrace noted that this tactic allowed the attacker to run cryptomining operations unnoticed until AI-driven anomaly detection flagged the unusual behavior.
Windows Character Map
Darktrace’s Findings
Darktrace’s detection models identified irregular system resource consumption and outbound connections linked to mining pools. The AI system flagged the behavior as anomalous when compared with baseline activity for the customer’s retail network.
The attempted attack was quickly contained before major disruption occurred, preventing long-term resource drain. However, Darktrace warned that similar attacks could succeed in less monitored environments.
Broader Cryptomining Trends
While cryptojacking incidents have declined since their 2018 peak, security analysts say the practice remains profitable when scaled across thousands of machines. Attackers increasingly embed mining scripts into compromised enterprise networks, IoT devices, and even cloud infrastructure.
The Windows Character Map exploit is part of a broader shift toward abusing obscure processes and trusted applications, making detection harder and extending the life span of cryptojacking campaigns.
The Windows Character Map cryptomining attack highlights how adversaries are refining their stealth strategies by embedding malicious operations into overlooked system utilities. Unlike data theft or ransomware, cryptojacking often flies under the radar but can still drain enterprise resources and rack up costs.
The July 2025 case illustrates that even low-profile processes are not immune to exploitation. As attackers refine these techniques, enterprises must strengthen behavioral monitoring and anomaly detection to identify threats that hide in plain sight.





