Researchers at LevelBlue Labs have detailed a new malware campaign that used a fileless loader to deliver AsyncRAT, a widely abused Remote Access Trojan known for credential theft and full remote control of compromised systems.
How the Attack Began
The investigation revealed that attackers gained initial access through a compromised ScreenConnect client. From there, the adversaries routed traffic through relay.shipperzone.online, a domain tied to unauthorized ScreenConnect deployments, to mask their activity.
Security vendor SentinelOne detected the unusual process execution, which provided visibility into the chain of events that followed.
Fileless Execution Chain
Once inside, the attackers executed a malicious VBScript named Update.vbs with WScript. The script launched PowerShell commands that downloaded two payloads — logs.ldk and logs.ldr — from an external server.
Instead of writing traditional files to disk, both payloads were placed in the public user directory and executed directly in memory. This fileless execution method allowed the attackers to evade many endpoint security controls.
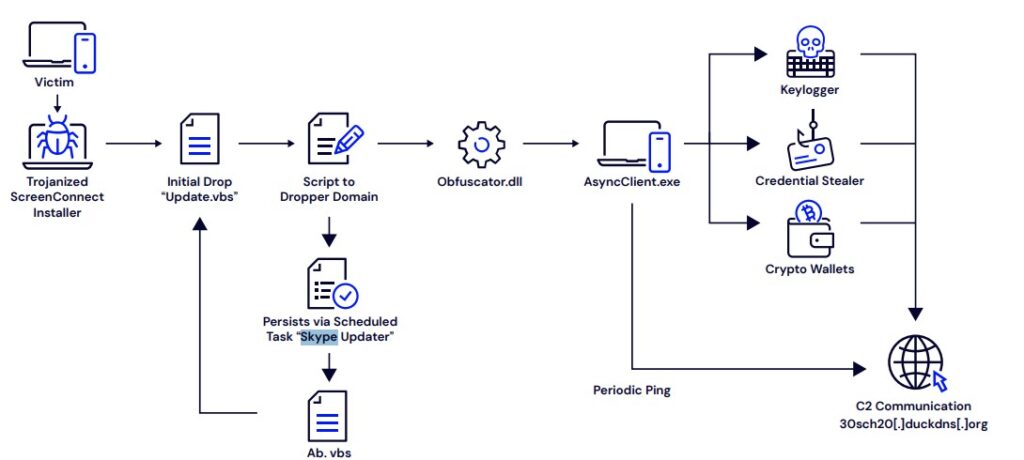
Attack Flow (Source: LevelBlue Labs)
AsyncRAT Deployment
The final stage of the attack dropped AsyncRAT, a Remote Access Trojan that provides attackers with extensive control over the infected host. Once active, AsyncRAT enabled adversaries to:
- Steal saved credentials and authentication tokens
- Capture keystrokes and clipboard data
- Access and exfiltrate system files
- Execute arbitrary commands remotely
- Deploy additional malware payloads
Because AsyncRAT is open source and widely available, it continues to be a favorite among both low-level cybercriminals and advanced threat groups.
Why Fileless Malware Matters
Fileless malware is particularly dangerous because it avoids writing persistent files to disk, leaving few forensic traces behind. By relying on scripts and memory-based execution, attackers significantly reduce their chances of detection by traditional antivirus or signature-based defenses.
The use of legitimate tools like ScreenConnect also complicates detection, as network administrators may mistake malicious activity for authorized remote sessions.
LevelBlue’s Findings
LevelBlue Labs confirmed that the attackers combined multiple evasion techniques, from abusing remote desktop software to obfuscating payload delivery. The researchers emphasized that AsyncRAT’s credential theft capabilities were likely the primary motive, though compromised systems could also be leveraged for persistence or lateral movement.
“This campaign highlights how attackers are increasingly blending fileless malware with legitimate tools to bypass defenses,” LevelBlue noted in its report.
The AsyncRAT fileless malware campaign demonstrates how attackers continue to refine their tactics to stay ahead of security controls. By combining fileless techniques, compromised remote access software, and powerful RAT capabilities, adversaries create a stealthy and highly effective attack chain.
For enterprises, this case emphasizes the need to monitor not just files but also processes, memory execution, and remote access tools. As fileless threats grow more common, security strategies must evolve to focus on behavior and anomalies rather than signatures alone.





