Microsoft’s Digital Crimes Unit (DCU) has dismantled a major phishing-as-a-service operation known as RaccoonO365, which stole thousands of Microsoft 365 credentials and targeted victims worldwide, including U.S. healthcare organizations. The takedown, announced on September 16, 2025, was made possible through a court order from the Southern District of New York.
How RaccoonO365 Worked
RaccoonO365, which Microsoft tracks as Storm-2246, operated as a subscription service for cybercriminals. It offered ready-to-use phishing kits designed to mimic official Microsoft login pages and emails. Even attackers with little or no technical skills could launch convincing phishing campaigns using the platform.
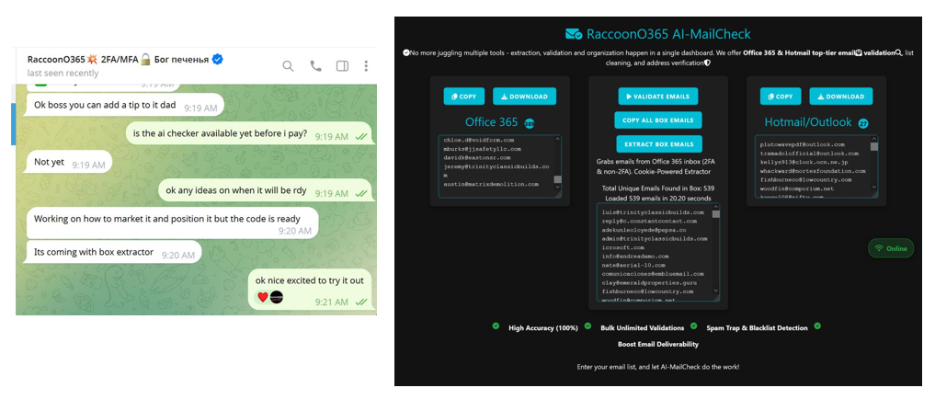
RaccoonO365 AI-MailCheck (Source: Microsoft)
Subscribers gained access to templates, hosting services, and automated tools to harvest Microsoft 365 usernames and passwords. The stolen credentials were then resold, reused for business email compromise (BEC), or leveraged for further intrusions.
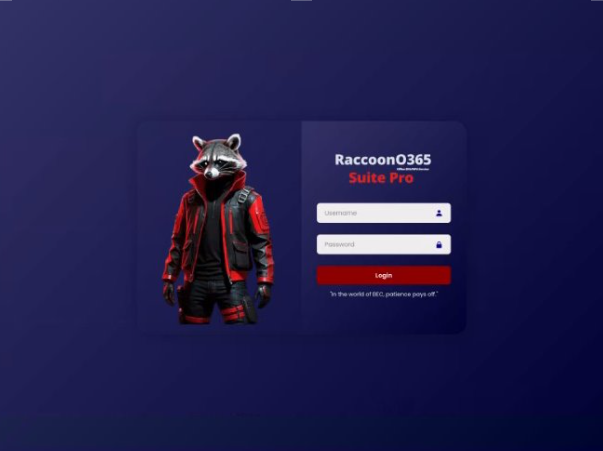
RaccoonO365 Login Page (Source: Microsoft)
Global Reach of the Service
Since July 2024, RaccoonO365 has been linked to the theft of at least 5,000 Microsoft credentials across 94 countries. One of its largest campaigns was a tax-themed phishing wave that targeted over 2,300 organizations in the U.S., including healthcare providers.
While not every stolen password led to a full compromise, the scale of the theft highlights the growing threat posed by phishing-as-a-service ecosystems.
Microsoft’s Legal Action
Through its DCU, Microsoft obtained a court order to seize 338 websites used to host RaccoonO365 phishing kits. By disabling these sites, the company disrupted the service’s infrastructure, limiting attackers’ ability to run campaigns.
“By dismantling the RaccoonO365 infrastructure, we are helping protect customers and raising the costs for cybercriminals who depend on these phishing services,” Microsoft stated in its announcement.
The company also shared indicators of compromise (IOCs) with global partners to help organizations detect related activity in their environments.
Why Healthcare Was Targeted
Researchers noted that U.S. healthcare organizations were frequently targeted because of their reliance on Microsoft 365 for communications and data storage. Stolen credentials from these sectors can be used to access sensitive medical data, billing systems, and personal health information (PHI).
The sector’s large attack surface and high-value data make it a recurring target for both financially motivated and nation-state actors.
Phishing-as-a-Service on the Rise
The RaccoonO365 case illustrates the growing professionalization of phishing operations. By offering subscription models, phishing groups lower the barrier to entry, enabling a wider pool of criminals to launch attacks.
This model mirrors ransomware-as-a-service (RaaS), where operators provide the infrastructure and tools while affiliates run the campaigns. For law enforcement and defenders, this approach complicates attribution and multiplies the scale of attacks.
Protecting Against Microsoft Credential Theft
Security experts recommend organizations take proactive steps:
- Enable multi-factor authentication (MFA) for all Microsoft accounts.
- Use phishing-resistant MFA methods like FIDO2 keys where possible.
- Train employees to recognize phishing emails that mimic Microsoft branding.
- Monitor login attempts for unusual geographies or devices.
- Regularly audit account permissions and credentials for compromise.
Microsoft also urged organizations to report suspected phishing domains and review logs for signs of credential theft.
The takedown of RaccoonO365 is a significant win against phishing-as-a-service operators. By seizing 338 domains, Microsoft not only disrupted ongoing campaigns but also sent a warning to similar groups that rely on infrastructure in U.S. jurisdictions.
However, experts caution that new services will inevitably emerge. For enterprises, the case underscores the importance of strong authentication, employee awareness, and constant vigilance against credential-based attacks.





