Security researchers at Zscaler ThreatLabz have uncovered two malicious packages on the Python Package Index (PyPI) that delivered a Remote Access Trojan named SilentSync to Windows systems. The campaign, attributed to an uploader using the handle CondeTGAPIS, highlights the continuing risk of supply-chain attacks inside the Python ecosystem.
Zscaler analysts Manisha Ramcharan Prajapati and Satyam Singh found the packages embedded a downloader and staging logic that fetched SilentSync and executed it in-memory. PyPI removed the packages after disclosure, but developers who installed the libraries may still face credential theft, data exfiltration, and system compromise.
How the attack worked
The attacker published two packages to PyPI that mimicked legitimate projects to blend into developer workflows. One package — sisaws — impersonated the legitimate sisa package (used by Argentina’s health information system). The malicious __init__.py included a function called gen_token() which acted as a downloader: it sent a hard-coded token to an attacker-controlled endpoint and received a secondary token, then used that exchange to pull the next-stage payload.
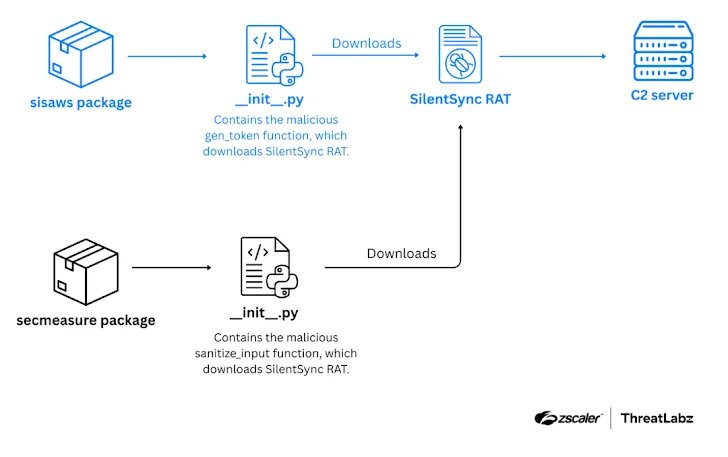
Attack flow (Source: ZScaler.com)
After the downloader ran, SilentSync executed and provided full RAT capabilities: remote command execution, file collection and exfiltration, screen capture, and persistent backchannel communications. Zscaler observed SilentSync extract browser data (credentials, cookies, autofill, history) from Chrome, Brave, Edge and Firefox — giving attackers immediate access to stored tokens and session cookies that often bypass MFA protections.
Why Python developers and PyPI are at risk
PyPI serves millions of developers and teams. Attackers rely on two facts: developers frequently install packages with minimal vetting, and automation (CI/CD, build pipelines) often pulls dependencies automatically. By naming a malicious library similarly to a trusted package and hiding the downloader inside an init function, the attackers increased the chance of accidental installs.
Supply-chain risks escalate when CI systems run package installs with elevated permissions or when repositories store secrets that get used during builds. A compromised package can turn a single developer workstation into a pivot point into corporate networks and cloud accounts.
Zscaler’s findings and scale
Zscaler reported that both malicious packages are no longer available on PyPI. Their analysis shows the attacker used lightweight obfuscation and simple token exchanges to avoid obvious detection. The gen_token() pattern mimicked legitimate API interactions, helping the payload look benign during cursory inspection.
While Zscaler hasn’t published wide telemetry on installation counts, the nature of the targeted libraries — one impersonating a national health system package — suggests the attacker aimed for trust-based trickery rather than broad-volume commodity malware. That tactic increases success rates among developers who expect specific packages and may install by name.
Immediate mitigation steps for developers and teams
If your project installed recent or unvetted PyPI packages, act quickly:
- Audit dependency trees: run
pip list --outdated/pipdeptreeand inspect new or suspicious packages in recent commits. - Rotate exposed credentials: assume any credentials present on developer machines, CI, or repositories that used the package could be compromised. Rotate tokens and invalidate suspicious sessions.
- Revoke CI secrets: replace tokens used in build agents and rotate API keys that might be stored in pipeline variables.
- Pin and cache dependencies: use lockfiles (
pip-compile,poetry.lock) and internal package caches/mirrors to avoid pulling unvetted packages directly from PyPI. - Deploy SCA and secrets scanning: integrate software composition analysis and secret-scanning into PR checks to detect dodgy packages and accidental key leaks.
- Run memory and behavior detection: use EDR/EDR-like tools that detect in-memory execution, PowerShell abuse, or unusual outbound connections to unknown domains.
- Harden CI privileges: apply least-privilege to runners; avoid running installs as privileged users and restrict network egress from build agents.
Longer-term protections
Organizations should adopt internal package registries (Artifactory, Nexus, or a private PyPI mirror) and apply mandatory vetting for packages used in production. Encourage developers to verify package maintainers, past release histories, and repository activity before adding new dependencies. Treat every third-party library as code you inherit and audit accordingly.
SilentSync’s delivery via PyPI proves attackers still prefer the path of least resistance: trusted ecosystems and human assumptions. Python developers and DevOps teams remain high-value targets because a single malicious dependency can cascade through builds into production. As supply-chain attacks grow more sophisticated, defenders must combine automation (SCA, secrets scanning) with human review and stricter CI controls.





