A cyber-espionage campaign attributed to Iranian threat actor UNC1549 has compromised 34 devices across 11 telecommunications companies, according to new research from Swiss cybersecurity firm PRODAFT. The group, also tracked as Subtle Snail, used LinkedIn recruitment-themed lures to deliver a custom backdoor called MINIBIKE, bypassing detection through infrastructure proxied via Microsoft Azure.
How the Campaign Worked
UNC1549, also known as TA455, impersonated HR representatives from legitimate organizations on LinkedIn. By posing as recruiters, the attackers engaged targeted employees and persuaded them to interact with malicious content.
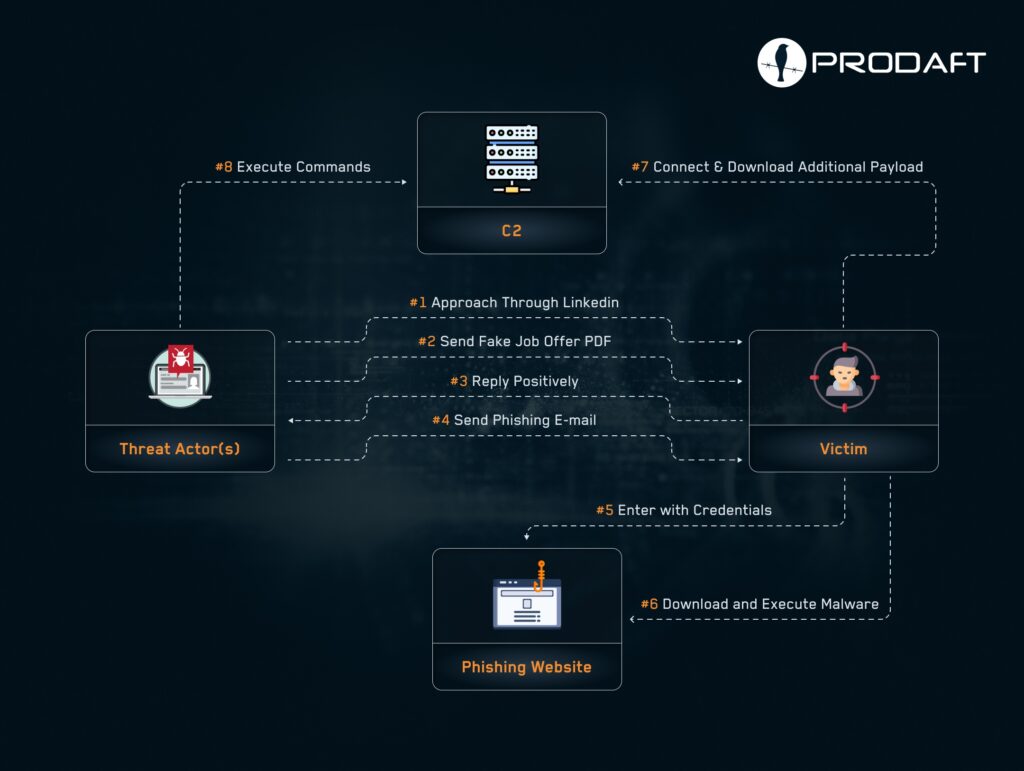
Initial access chain of attacks. (Source: prodaft.com)
Once contact was established, the adversaries delivered malware disguised as job-related files. These files deployed a variant of the MINIBIKE backdoor, which communicated with command-and-control (C2) infrastructure hidden behind Azure cloud services. This technique helped the attackers blend in with normal enterprise traffic, reducing the likelihood of detection.
Scope of the Attack
PRODAFT’s report confirmed that UNC1549 successfully infiltrated 34 devices in 11 telecom firms located in:
- Canada
- France
- The United Arab Emirates
- The United Kingdom
- The United States
The focus on telecommunications is consistent with Iran-linked groups’ long-term interest in collecting intelligence from strategic infrastructure sectors.
Malware Used: MINIBIKE
The MINIBIKE backdoor provides attackers with remote control over compromised systems. Once installed, it enables:
- Execution of arbitrary commands
- Data exfiltration
- File system access and manipulation
- Installation of additional payloads
By deploying MINIBIKE through LinkedIn job lures, UNC1549 combined social engineering with stealthy malware operations to achieve persistence inside high-value targets.
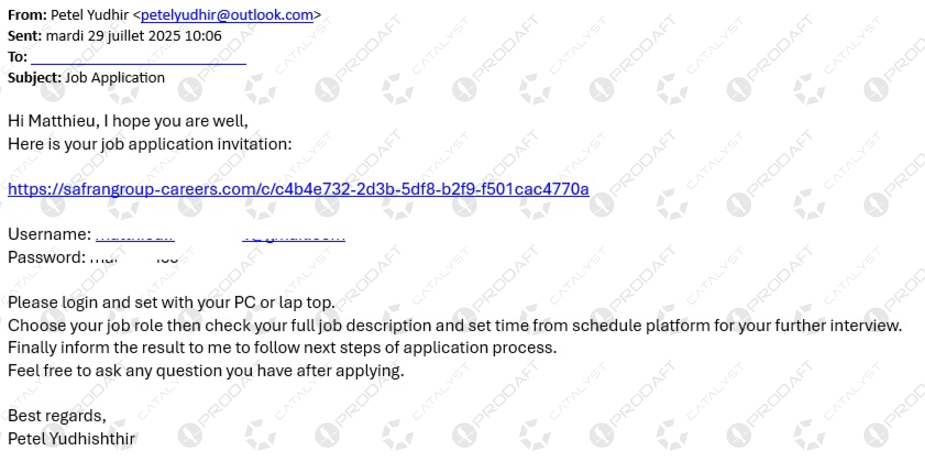
Example of Phishing Email (Source: prodaft.com)
Links to Other Iranian Groups
Researchers noted overlaps between UNC1549 and other Iranian espionage clusters, including:
- Smoke Sandstorm
- Crimson Sandstorm (also known as Imperial Kitten, TA456, Tortoiseshell, and Yellow Liderc)
Google-owned Mandiant first documented UNC1549 in February 2024, and Israeli cybersecurity firm ClearSky later detailed its use of job-themed phishing to target the aerospace industry in 2023. Those campaigns delivered malware families such as SnailResin and SlugResin, showing UNC1549’s broader interest beyond telecom.
Strategic Motivation
According to PRODAFT, UNC1549’s primary motivation is espionage. By infiltrating telecom firms, the group can intercept communications, monitor networks, and exfiltrate sensitive operational data. The group also continues to maintain interest in aerospace and defense sectors, suggesting broader strategic goals aligned with Iran’s intelligence objectives.
“The group’s primary motivation involves infiltrating telecommunications entities while maintaining interest in aerospace and defense organizations to establish long-term persistence and exfiltrate sensitive data for strategic espionage purposes,” PRODAFT said.
Why LinkedIn Is Targeted
Social networks like LinkedIn provide a trusted environment where employees expect to receive career-related inquiries. Attackers exploit this trust by crafting job-themed lures that feel authentic and professional.
By combining LinkedIn engagement with malware delivery, UNC1549 bypasses traditional email-based phishing defenses. This tactic continues to prove effective across industries, particularly in high-value sectors such as telecom and aerospace.
Defending Against LinkedIn Malware Lures
Security experts recommend organizations:
- Train employees to scrutinize unsolicited LinkedIn job offers or recruiter messages.
- Monitor for unusual outbound traffic to cloud services like Azure that could mask C2 activity.
- Deploy endpoint detection capable of catching RAT behavior like MINIBIKE.
- Enforce strict separation between corporate and personal accounts to reduce social engineering risk.
- Review threat intelligence feeds for IOCs linked to UNC1549 infrastructure.
The UNC1549 campaign underscores the growing sophistication of Iran-linked espionage groups. By blending social engineering, cloud-based infrastructure, and stealthy backdoors, adversaries continue to bypass traditional defenses and establish long-term footholds in sensitive industries.
For telecommunications companies, the compromise of 34 devices is a reminder that adversaries target employees as the first step to infiltrating entire networks. For the wider industry, the case illustrates how LinkedIn remains one of the most abused platforms for cyber-espionage operations.





