Google has released its September 2025 Android security update, patching 120 vulnerabilities, including two zero-day flaws already exploited in targeted attacks. The update addresses weaknesses across multiple Android components, with fixes available for devices running supported versions.
The Two Zero-Days Under Attack
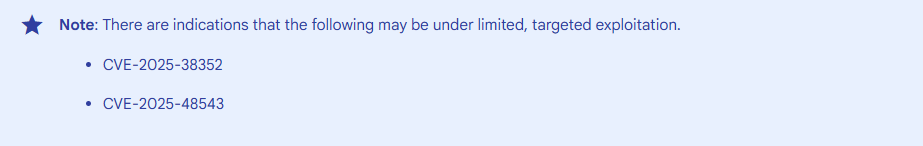
Google confirmed active exploitation of two privilege escalation flaws:
CVE-2025-38352 — A Linux Kernel vulnerability (CVSS score: 7.4) that allows local privilege escalation without requiring user interaction.
CVE-2025-48543 — A flaw in the Android Runtime component that also enables local privilege escalation with no additional execution privileges needed.
Both vulnerabilities are classified as zero-days, meaning attackers were exploiting them before patches became available. Google has not disclosed details of the campaigns but noted they involved targeted attacks, suggesting high-value individuals or organizations were the focus.
Scope of the Update
Beyond the zero-days, the September bulletin patched a total of 120 security issues across the Android ecosystem. These spanned components including:
- Framework
- Media Framework
- System libraries
- Google Play system updates
The flaws ranged from moderate to critical severity, with potential impacts such as privilege escalation, data exfiltration, and remote code execution.
(Source: Android Security)
Why These Flaws Matter
Privilege escalation vulnerabilities are particularly dangerous because they allow attackers to move from limited access to full system control. Combined with other exploits, they can let adversaries install spyware, steal sensitive data, or maintain persistence on a device.
The fact that both zero-days required no user interaction increases their severity. Unlike phishing-based threats, these exploits could compromise a device without the victim clicking links or opening files.
Who Is Affected
Any Android device that has not yet applied the September 2025 security patch remains at risk. Google has already distributed fixes to its Pixel devices, while other vendors will roll out updates depending on their patch schedules.
Given the history of delayed patch adoption across the Android ecosystem, millions of devices may remain exposed for weeks or months.
Google’s Response
In its advisory, Google encouraged all users to update immediately, emphasizing that patching zero-days is critical to device security. The company also highlighted improvements in Google Play system updates, which allow some fixes to be delivered independently of OEM updates.
Google did not attribute the active exploitation to a specific threat actor but is sharing technical details with security researchers and device makers.
Expert Reactions
Security analysts warned that attackers increasingly target Android vulnerabilities due to the operating system’s massive global user base. State-sponsored groups and commercial spyware vendors frequently rely on privilege escalation flaws to gain full device access.
“Two Android zero-days in the same patch cycle shows how attractive the platform is to attackers,” one researcher said. “Users should update immediately and enterprises should enforce patch compliance for all managed devices.”
The September 2025 update underscores the importance of timely Android patching. With over 120 flaws fixed and two zero-days already exploited in the wild, users who delay updating remain exposed to serious risks.
For individuals, updating quickly is the only defense. For enterprises, the incident highlights the need for strict mobile device management policies to reduce the window of exposure when zero-days are disclosed.





