Recent research from CloudSEK reveals the growing sophistication of the Androxgh0st botnet, which is now targeting academic institutions such as UC San Diego. The malware uses remote code execution (RCE) vulnerabilities and web shells to infiltrate systems. Learn how this evolving threat operates — and what steps you can take to defend against it.
CloudSEK’s latest investigation, shared with Hackread.com, reveals a notable evolution in the Androxgh0st botnet’s tactics and reach. Originally detected in early 2023, the botnet has steadily grown more advanced, now employing a broader range of initial access methods. Among its latest strategies is the exploitation of poorly secured or misconfigured servers, particularly those operated by academic institutions. This shift marks a concerning escalation in both scope and technical sophistication.
In January 2024, the U.S. Cybersecurity and Infrastructure Security Agency (CISA) issued a public advisory, highlighting the growing threat posed by the Androxgh0st botnet. The alert aimed to raise awareness about its expanding capabilities and increasing number of targeted systems.
Targeted Systems and Attack Methods
Recent analysis by CloudSEK reveals that the Androxgh0st botnet has significantly broadened its attack surface, increasing its known exploitation methods by around 50% since early 2024. One alarming discovery was a command-and-control (C2) logger panel operating from a subdomain linked to the University of California, San Diego. This domain, oddly tied to content for the USA Basketball Men’s U19 National Team, highlights the botnet’s ability to infiltrate unexpected and seemingly unrelated infrastructure.
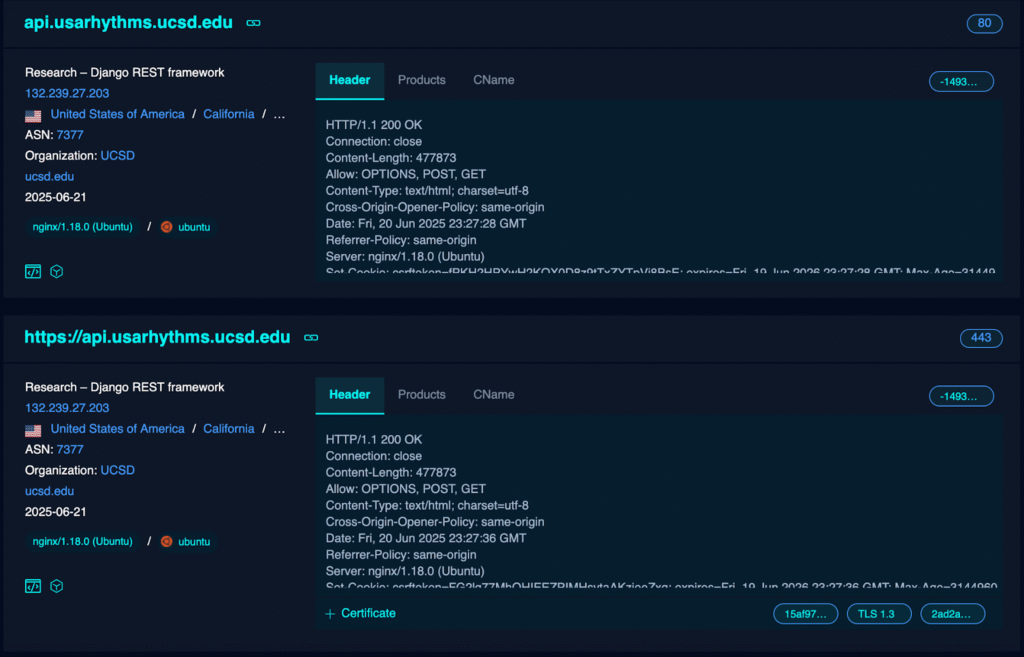
Androxgh0st botnet’s (C&C) (Via CloudSEK)
The tactic of hijacking legitimate yet vulnerable domains continues to gain traction among botnet operators. By embedding their infrastructure within trusted public platforms, attackers can more effectively blend in with regular web traffic, evading traditional security filters. In earlier instances, the Androxgh0st botnet was seen hosting its command infrastructure on platforms like a Jamaican event aggregator, further illustrating this deceptive approach.
Androxgh0st takes advantage of several high-profile security flaws in widely used technologies, including Apache Shiro, the Spring Framework, various WordPress plugins, and Lantronix IoT devices. By targeting these vulnerabilities, the botnet can execute unauthorized code, extract sensitive data, and even hijack system resources for tasks like cryptocurrency mining — making its impact both broad and severe.
In its inaugural report, CloudSEK anticipated that the operators behind the Androxgh0st botnet would enhance their arsenal by incorporating new malicious software into their toolkit by the middle of 2025. This foresight now appears to be materializing, as recent developments suggest the prediction is unfolding as expected.
Breaking Down the Botnet’s Capabilities
The latest report from the company reveals that the Androxgh0st botnet employs a variety of Initial Access Vectors (IAVs) to infiltrate systems, serving as entry points for unauthorized access. Once inside, the attackers establish communication with compromised devices through Command-and-Control (C2) servers. Their primary objective is achieving Remote Code Execution (RCE), which allows them to execute malicious code on targeted systems remotely.
Androxgh0st frequently employs sophisticated techniques such as JNDI Injection and OGNL Injection, which are particularly potent against Java-based applications. These advanced methods enable the botnet to circumvent security measures and establish persistent control, often by deploying webshells on compromised systems.
How to Stay Secure Against Androxgh0st
Given these emerging threats, organizations, particularly academic institutions and those utilizing impacted software, are strongly encouraged to act swiftly. CloudSEK advises promptly applying patches to all systems exposed to known CVEs, including those associated with Spring4Shell and Apache Shiro vulnerabilities.
To mitigate Androxgh0st threats, organizations should limit outbound network traffic for protocols such as RMI, LDAP, and JNDI. Additionally, conducting regular audits of website plugins, such as WordPress’s Popup Maker, and vigilantly monitoring for suspicious file activity are essential measures for preventing and identifying potential compromises.
“The botnet has shifted from primarily targeting Chinese-linked surveillance operations to adopting a broader and more aggressive exploitation approach,” explained Koushik Pal, Threat Researcher at CloudSEK. “It’s now leveraging a wide range of critical vulnerabilities such as JNDI injection and OGNL exploits, including CVEs associated with popular frameworks like Apache Shiro, Spring, and Fastjson.”





