Apple has introduced a new security feature called Memory Integrity Enforcement (MIE) in its latest devices — the iPhone 17 and iPhone Air — powered by the company’s new A19 and A19 Pro chips. The feature promises always-on memory safety protection designed to stop advanced spyware and exploit attempts at their root.
What Memory Integrity Enforcement Does
Apple described Memory Integrity Enforcement as a defense mechanism that continuously enforces memory safety across critical attack surfaces. Specifically, it protects:
- The kernel, a frequent target for privilege escalation
- More than 70 userland processes tied to everyday iOS functions
Unlike traditional security add-ons, MIE is built directly into the A19 chips. Apple said the architecture was designed to maintain strong security protections without sacrificing device performance, a common tradeoff in memory safety systems.
The Technology Behind MIE
Apple said MIE builds on its secure memory allocators and integrates the Enhanced Memory Tagging Extension (EMTE) in synchronous mode. It is further reinforced by Tag Confidentiality Enforcement policies, which prevent attackers from bypassing protections by manipulating memory tags.
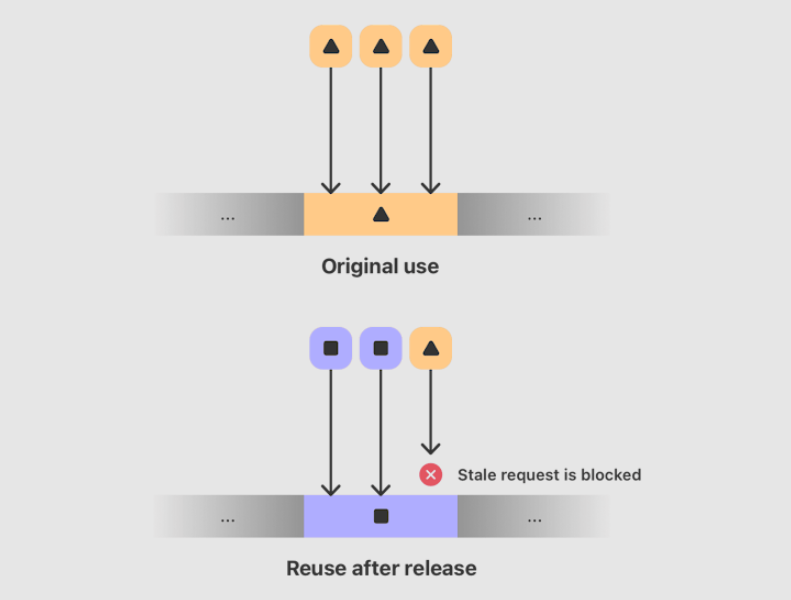
MIE blocks use after free access.
In practice, MIE ensures that memory corruption errors — often exploited by spyware vendors — are blocked before they can execute malicious code. This makes it significantly harder for attackers to run exploits that rely on buffer overflows, use-after-free bugs, or other memory-related vulnerabilities.
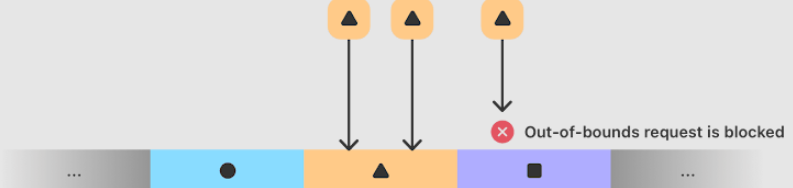
MIE blocks buffer overflows.
Why Apple Is Introducing It Now
The launch of iPhone 17 and iPhone Air comes amid rising concerns over spyware targeting iOS devices, including state-sponsored surveillance tools that exploit zero-day vulnerabilities.
By embedding MIE into the hardware, Apple aims to make such attacks dramatically harder to execute. Analysts believe the move is a direct response to the global spyware market, where advanced commercial surveillance tools continue to exploit memory safety flaws in mobile devices.
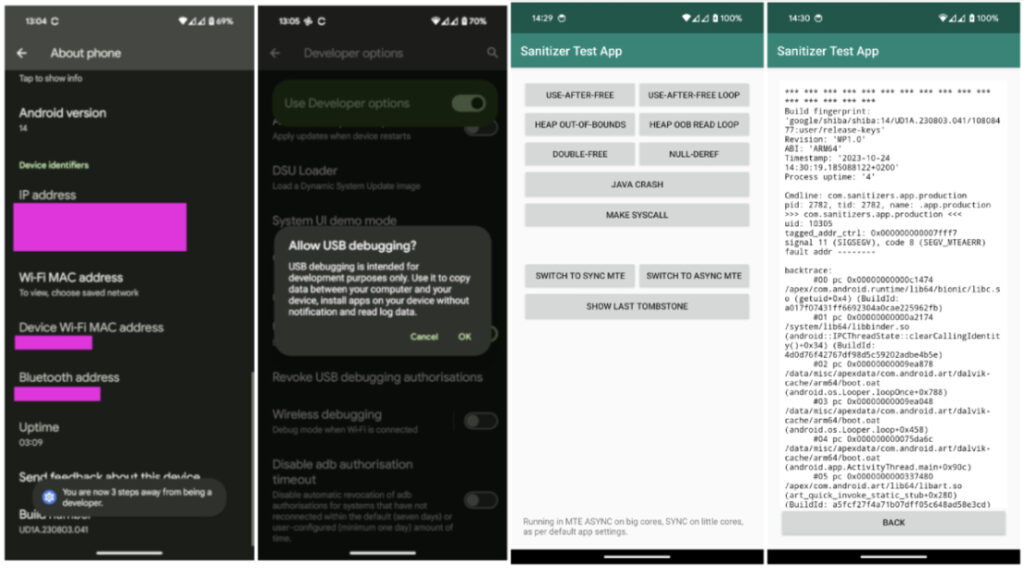
Enabling MTE on Google Pixel (Source: thehackernews.com)
Apple’s Statement
In its announcement, Apple highlighted the proactive nature of MIE:
“Memory Integrity Enforcement is built on the robust foundation provided by our secure memory allocators, coupled with Enhanced Memory Tagging Extension (EMTE) in synchronous mode, and supported by extensive Tag Confidentiality Enforcement policies.”
The company stressed that users should not notice performance degradation, since the A19’s architecture was optimized to handle the additional workload.
Security Industry Reactions
Security researchers welcomed the announcement, calling it one of the most significant hardware-level defenses in recent iPhone history.
“Apple is raising the bar for memory safety protections,” one analyst noted. “By making MIE always-on and hardware-backed, they’re cutting off entire exploit classes that spyware developers rely on.”
Experts also pointed out that while no system is invulnerable, forcing attackers to work around chip-level protections increases the cost and complexity of developing reliable iOS exploits.
For users, the iPhone 17 and iPhone Air represent more than just incremental performance upgrades. With MIE baked into the A19 chips, Apple is signaling that hardware-level security will be a defining feature of its future devices.
The move positions Apple as a leader in memory safety enforcement, directly addressing one of the most exploited weaknesses in modern operating systems. It also underscores a shift in the mobile security landscape, where chip design and software protections increasingly converge to combat sophisticated threats.





