A long-dormant macOS backdoor called ChillyHell has resurfaced, according to new research from Jamf Threat Labs. The malware, first documented in 2023, is once again active and evolving, showing signs that threat actors are refining their tactics to bypass Apple’s defenses.
ChillyHell’s History
ChillyHell was first uncovered in 2023 by Mandiant, which linked it to UNC4487, a threat actor previously tied to a campaign against a Ukrainian auto insurance website. That attack delivered the MATANBUCHUS loader, known for establishing persistent access to compromised systems.
Although ChillyHell appeared dormant for a period, Jamf researchers confirmed the backdoor never fully disappeared. Instead, it has quietly reemerged with new variants, targeting Intel-based Macs.
The New Sample
On May 2, 2025, a new ChillyHell sample was uploaded to VirusTotal. Researchers noted that the malware initially registered a “zero” detection score, meaning no antivirus engines flagged it as malicious. Such stealth is highly unusual for a known malware family, underscoring its ability to slip past defenses.
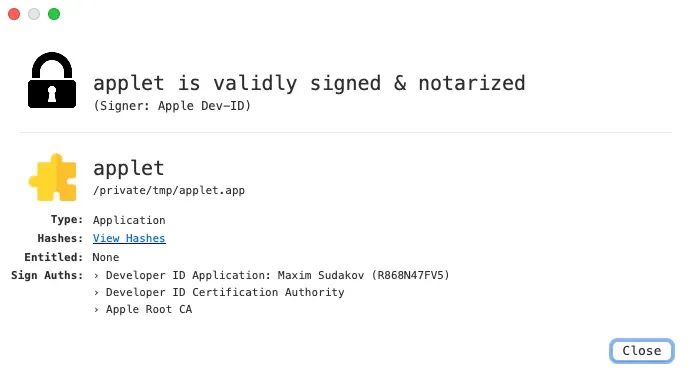
Image (Scoure: jamf.com)
Jamf’s analysis revealed that ChillyHell uses Google.com as a decoy domain, blending malicious communications with legitimate web traffic to avoid detection. The malware establishes persistence, survives reboots, and allows attackers to execute commands remotely, giving them long-term control of a compromised Mac.
How It Works
The malware operates as a macOS backdoor with multiple capabilities:
- Bypasses macOS security checks to install silently\
- Embeds itself for persistence across reboots
- Exfiltrates files and system data
- Executes remote commands to install additional payloads
- Uses legitimate domains (like Google.com) as cover traffic
By leveraging trusted domains, ChillyHell disguises its network activity and blends into normal traffic patterns. This makes it significantly harder for defenders to distinguish between benign and malicious connections.
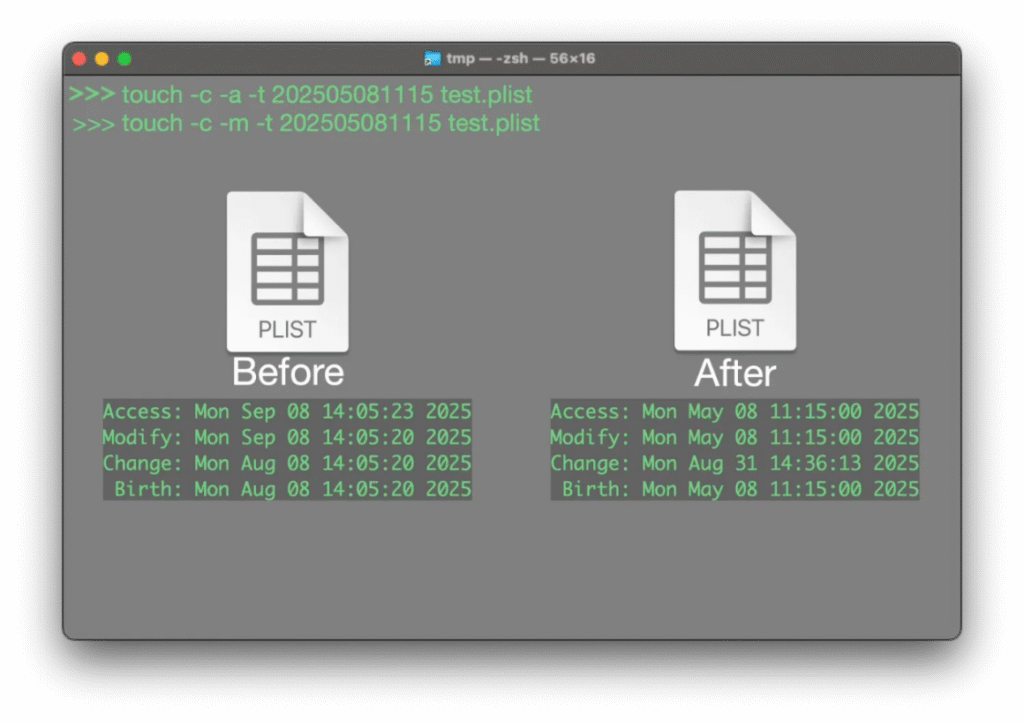
Image (Source: jamf.com)
Why Intel-Based Macs Are Targeted
The latest variant is specifically built for Intel Macs, even as Apple transitions toward Apple Silicon. Researchers believe attackers may still see value in targeting Intel systems because many enterprise environments continue to rely on them.
By focusing on Intel-based hardware, ChillyHell operators can compromise older devices that may not receive the latest security patches or hardware protections.
Jamf’s Findings
Jamf confirmed that the malware’s persistence mechanisms and obfuscation techniques have improved since earlier versions. These upgrades demonstrate ongoing development and suggest the threat actors remain committed to maintaining the malware family.
“The zero-detection score is a reminder that even well-documented threats can evolve into new, harder-to-detect variants,” Jamf noted.
The resurgence of ChillyHell malware shows that macOS is not immune to advanced threats. While Apple continues to strengthen security in newer devices, persistent malware families adapt quickly, exploiting gaps in legacy hardware and user behavior.
For enterprises, the threat highlights the importance of visibility across mixed Mac environments, including older Intel-based models. For individuals, it serves as a reminder that malware can disguise itself behind trusted domains and evade traditional antivirus protections.





