Cloudflare has confirmed a data breach affecting customer support case data, following the exploitation of its Salesforce environment through the Salesloft Drift supply chain attack. The company stressed that its core systems and infrastructure were not impacted, but sensitive case information tied to customer support was exposed.
How the Breach Happened
According to Cloudflare’s advisory, attackers gained unauthorized access after exploiting stolen OAuth tokens connected to the Salesloft Drift chatbot. The integration, designed to let website visitors communicate directly with Cloudflare’s support team, was abused by threat actors to infiltrate the Salesforce environment.
The threat group behind the intrusion, which Cloudflare identified as GRUB1, leveraged the compromised OAuth tokens to extract support case details. The exposed information included communications between customers and Cloudflare support, account metadata, and potentially sensitive diagnostic data.
Scope of Exposure
Cloudflare confirmed that only its Salesforce support environment was impacted. The attackers did not access production systems, internal networks, or security infrastructure that protect customer websites and services.
Even so, the compromised case data could reveal valuable information to adversaries, such as:
- Technical details about customer deployments
- Email addresses and account identifiers
- Logs or screenshots submitted during troubleshooting
- Context that could aid in future spear-phishing or targeted attacks
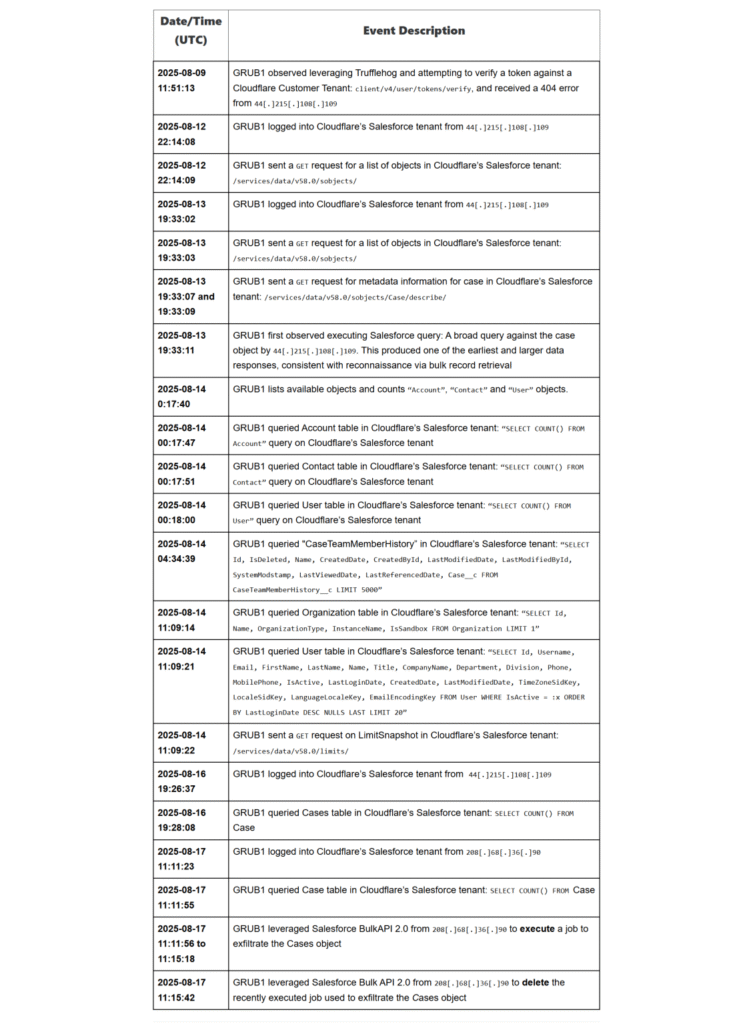
Detailed event timeline (Source: Cloudflare)
Part of a Larger Campaign
The breach was linked to the Salesloft Drift supply chain attack, which affected hundreds of companies that integrated the tool into Salesforce. By compromising OAuth tokens, attackers bypassed normal authentication controls, enabling lateral access into corporate support systems.
Security analysts said the campaign shows the fragility of SaaS integrations. By chaining together third-party tools like Drift and Salesforce, attackers can move across environments to harvest sensitive information without ever touching core infrastructure.
Cloudflare’s Response
Cloudflare said it revoked the stolen OAuth tokens, cut off malicious access, and worked with both Salesforce and Salesloft to investigate the incident. The company also notified affected customers and is providing guidance on how to monitor for suspicious follow-up activity.
“We want to reassure our customers that their websites, networks, and Cloudflare services remain fully secure,” the company stated. “This incident was limited to support case data within Salesforce, but we recognize the sensitivity of this information and are treating it with the highest priority.”
Risks to Customers
While the breach did not compromise production systems, the exposed data may still enable social engineering or targeted phishing. Threat actors can use support case details to craft convincing lures that reference prior customer interactions with Cloudflare.
GRUB1’s motives remain unclear, though researchers believe the group’s focus on OAuth exploitation signals a broader campaign targeting SaaS ecosystems. The group’s tactics align with recent identity-focused operations carried out by advanced persistent threat actors.
The Cloudflare data breach highlights the growing risk of third-party SaaS integrations in enterprise security. Even when core systems are well protected, attackers are increasingly targeting connected platforms like Salesforce to extract sensitive data.
By abusing OAuth tokens, adversaries bypassed traditional login safeguards, echoing recent attacks against Microsoft and Google environments. Security experts warn that these identity-based supply chain attacks are escalating across industries.
For customers, the incident is a reminder that even non-production data, like support case details, can carry serious implications when leaked. For enterprises, the lesson is clear: SaaS connections must be continuously audited, monitored, and restricted to minimize exposure.