A revamped version of the DarkCloud Infostealer has reemerged, according to researchers at eSentire’s Threat Response Unit (TRU). The malware, now at version 4.2, is being actively marketed to cybercriminals and has already been spotted in attacks against the manufacturing sector.
DarkCloud’s Return
DarkCloud is not new, but the malware has undergone a complete rewrite. TRU analysts confirmed that version 4.2 was rewritten in Visual Basic 6 (VB6), signaling an effort to evade signature-based detection and improve compatibility across Windows environments.
During September 2025, eSentire intercepted an attempted deployment of DarkCloud against a customer in the manufacturing industry, where the malware attempted to exfiltrate credentials, cryptocurrency wallets, and contact data.

DarkCloud Website (Source: eSentire.com)
Capabilities of DarkCloud 4.2
The latest version of DarkCloud functions as a multi-purpose infostealer with the ability to:
- Steal browser credentials, cookies, and autofill data
- Harvest cryptocurrency wallet information
- Collect email addresses and contacts for spam or phishing campaigns
- Exfiltrate system information for profiling and resale
By targeting multiple data sources, DarkCloud provides cybercriminals with everything from immediate financial gain to long-term identity theft opportunities.
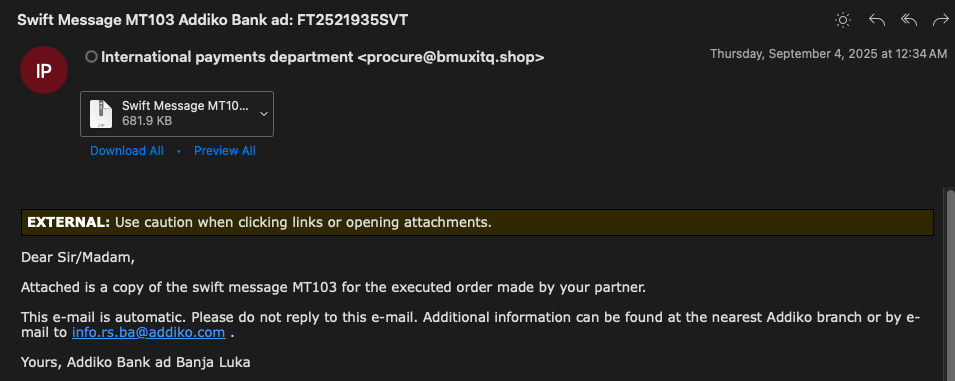
Phishing Lure Email (Source: eSentire.com)
DarkCloud’s Criminal Roots
Historically, DarkCloud was sold on the Russian cybercrime forum XSS.is, a hub for malware, exploits, and underground trade. In July 2025, law enforcement seized XSS.is and arrested a suspected administrator in Ukraine.
The takedown was short-lived. By July 24, 2025, the forum resurfaced on mirror and .onion domains, continuing to serve as a marketplace for cybercrime tools.
Today, DarkCloud has shifted its distribution model. It is sold on a dedicated site, darkcloud[.]onlinewebshop[.]net, and promoted on Telegram by a user calling themselves @BluCoder. This shift shows how malware developers adapt quickly when traditional dark web channels face disruption.
Why VB6 Matters
Rewriting DarkCloud in VB6 is unusual in modern malware development but gives the authors several advantages:
- Compatibility with older systems still common in enterprise environments
- Evasion of automated detection systems trained on modern languages
- Simpler obfuscation for payload delivery
This technical pivot highlights the developers’ intent to broaden the malware’s reach while slipping past defenses that rely heavily on pattern recognition.
Expert Concerns
Security researchers warn that DarkCloud’s reemergence reflects the resilience of infostealer markets. Even after major forums like XSS.is are seized, malware families quickly resurface under new distribution models.
“The relaunch of DarkCloud demonstrates how cybercriminals pivot to maintain revenue streams,” TRU researchers noted. “Its ability to steal credentials, crypto, and contact data makes it highly attractive to a wide range of threat actors.”
The reemergence of DarkCloud Infostealer 4.2 shows how cybercriminal groups rapidly adapt to law enforcement actions. Despite takedowns of underground forums, malware developers continue to market and sell their tools through new channels, from dedicated websites to messaging apps.
For enterprises, DarkCloud’s capabilities represent a direct threat to corporate credentials and financial assets. For individuals, the malware’s focus on crypto wallets and personal contacts highlights how infostealers are evolving to serve multiple criminal markets.





