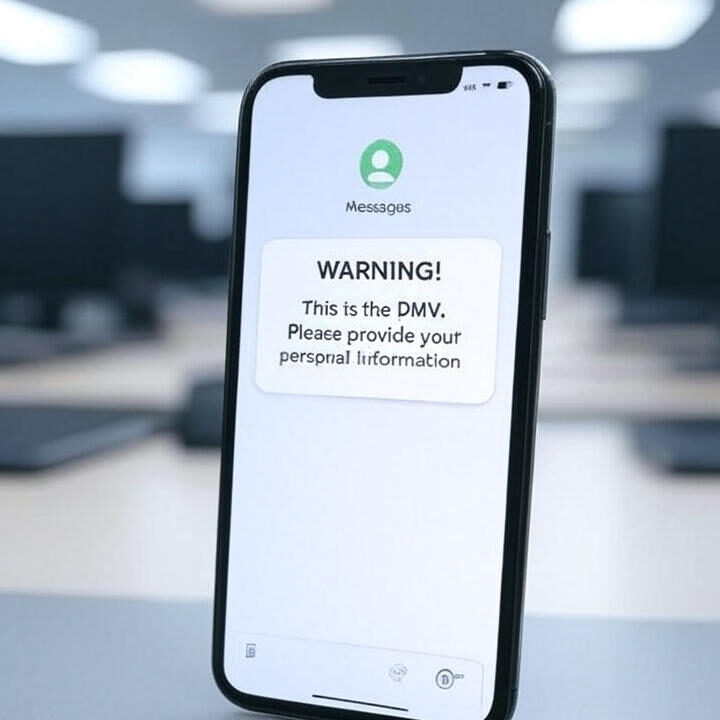
A sophisticated DMV phishing scam 2025 campaign is wreaking havoc across the United States, successfully deceiving thousands of drivers with convincing text messages that appear to originate from legitimate state motor vehicle departments. These fraudulent SMS attacks are harvesting everything from Social Security numbers to credit card details by exploiting Americans’ trust in official government communications—and the scammers are getting disturbingly good at mimicking authentic DMV correspondence.
Check Point researchers uncovered this sprawling DMV phishing scam 2025 operation in May, revealing a sophisticated infrastructure of spoofed SMS messages paired with meticulously cloned government websites. The attackers didn’t just send random texts—they crafted convincing replicas of state DMV portals and messaging systems, creating a multi-layered deception designed to harvest victim credentials by exploiting the inherent trust Americans place in their local motor vehicle authorities.
Unpaid Tolls and Threats of License Suspension
Victims of this DMV phishing scam 2025 reported receiving panic-inducing messages warning of unpaid toll violations or imminent driver’s license suspensions that demanded immediate action. The fraudulent texts contained links to state-specific website clones so visually convincing they replicated official DMV branding, color schemes, and even local contact information—creating a sense of urgency that bypassed victims’ normal skepticism about suspicious communications.
Once victims landed on these fraudulent DMV portals, the DMV phishing scam 2025 operators deployed a clever psychological trick—requesting minimal payments typically under $7 to resolve the supposed violation. This small fee served as digital camouflage for the real prize: comprehensive personal data harvesting that included full names, addresses, email accounts, phone numbers, and complete credit card details worth far more than the nominal “toll” payment on the black market.
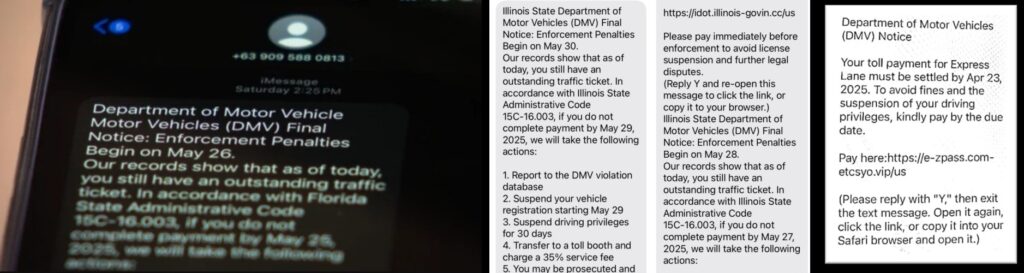
Examples of some of the fake DMV texts scam messages
A Well-Built Scam Network
The DMV phishing scam 2025 operation revealed a sophisticated, centralized command structure that went far beyond amateur fraud attempts. According to Check Point’s blog post, the attackers systematically replicated authentic state DMV URL patterns while hosting multiple fake domains on a single malicious IP address (49.51.75162)—an infrastructure already flagged for previous cybercriminal activities, suggesting this campaign emerged from an established threat actor with proven technical capabilities.
The scam targeted states with large populations, including:
- Texas
- Florida
- Georgia
- New York
- California
- New Jersey
- Pennsylvania
Each site used identical scripts, styling, and media, indicating a single development team—not scattered attackers—was behind the scam.
Evidence Points to China-Based Threat Actor
Check Point’s investigation traced this DMV phishing scam 2025 directly back to China-based threat actors through multiple digital fingerprints. The smoking guns included universal use of alidns.com name servers across all fraudulent domains, SOA contact emails registered through hichina.com infrastructure, and Chinese-language comments embedded within the malicious website source code—creating an unmistakable attribution trail pointing to organized cybercriminal operations originating from China.
Researchers tied the attack toolkit to “Lighthouse,” a phishing platform previously used by the Smishing Triad—an actor known for targeting U.S. DMVs.
While attribution is rarely certain, overlapping infrastructure, language, and tools suggest the scam is likely the work of a Chinese-speaking threat group.
This campaign follows a broader pattern of foreign-linked cyber activity targeting U.S. infrastructure. In a separate investigation, researchers recently uncovered the Androxgh0st botnet, which compromised university servers across the country using similar coordinated tactics.
Impact and Public Response
This DMV phishing scam 2025 has earned the dubious distinction of becoming one of the largest smishing (SMS phishing) operations to hit American soil this year. The FBI’s Internet Crime Complaint Center (IC3) documented over 2,000 related victim reports within just one month of the campaign’s peak activity, though cybersecurity experts warn this represents only the tip of the iceberg—with the actual number of compromised Americans likely reaching into the tens of thousands as many victims remain unaware their data was harvested.
Media coverage including CBS News reporting helped amplify public awareness of the DMV phishing scam 2025, forcing state agencies into damage control mode across the country. Multiple Department of Motor Vehicles and Department of Transportation websites rushed to publish official fraud warnings, explicitly advising residents to ignore any unsolicited text messages claiming toll violations or license issues—a coordinated response that highlighted just how widespread the fraudulent campaign had become.
What You Can Do
These scams rely on urgency, trust in government institutions, and low-dollar deception. To stay safe from similar phishing attacks:
- Block high-abuse domain extensions like .cfd and .win
- Follow DMV updates from verified sources only
- Type the DMV web address manually into your browser
- Never click suspicious links in SMS messages about fines or suspensions
- Report scam texts to 7726 (SPAM) and log incidents at reportfraud.ftc.gov