Cybersecurity researchers at Huntress have uncovered a malware campaign using a fake AnyDesk installer to spread MetaStealer, relying on the well-known ClickFix social engineering technique. The attack abuses Windows search and user trust in remote access tools to bypass security defenses.
How the Scam Works
The ClickFix method is a classic trick in which attackers convince victims to fix a fabricated issue by copying and pasting a command into the Windows Run dialogue box. Once executed, the command downloads and installs malware from an attacker-controlled server.
In this campaign, attackers hosted a fake AnyDesk installer that appears identical to the legitimate remote access tool. When victims search for AnyDesk online, malicious ads and poisoned search results redirect them to fraudulent websites distributing the trojanized installer.
Once installed, the payload drops MetaStealer, an infostealer malware designed to extract sensitive data from the system.
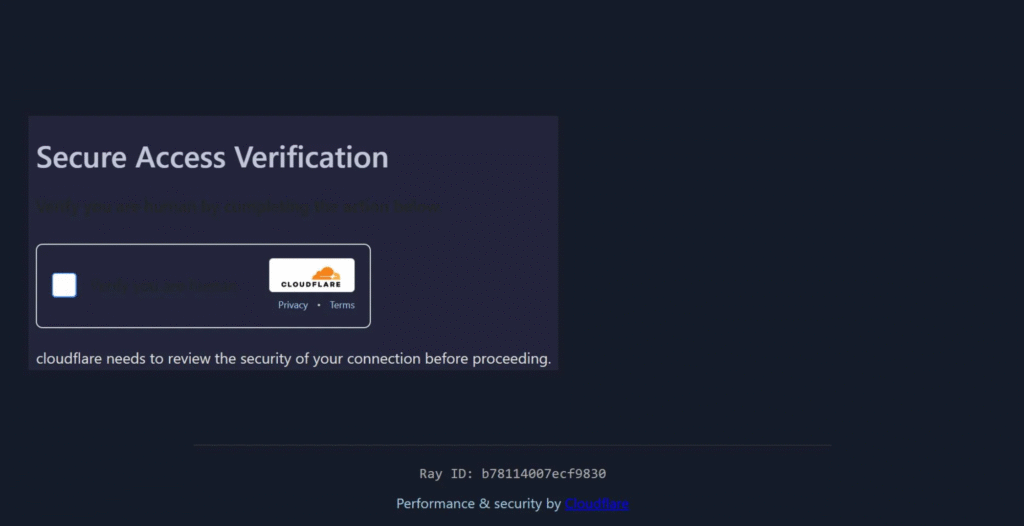
Initial link that redirects users to a fake Cloudflare turnstile (Source: Huntress.com)
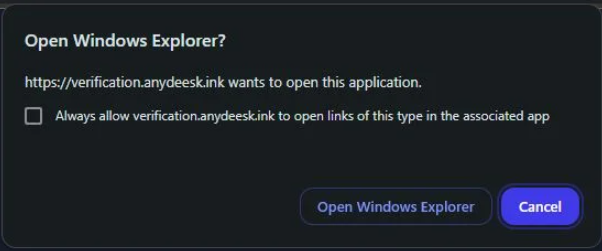
Attack chain redirects users to a prompt asking to Open Windows File Explorer (Source: Huntress.com)
What MetaStealer Steals
MetaStealer focuses on exfiltrating personal and corporate data, including:
- Browser cookies and saved login credentials
- Cryptocurrency wallet keys
- Authentication tokens for SaaS apps
- System details and device fingerprints
Researchers noted that MetaStealer communicates with attacker-controlled infrastructure to continuously exfiltrate data, giving adversaries long-term access to compromised accounts.
Why AnyDesk Was Chosen
AnyDesk is a legitimate and widely used remote access tool, popular among IT teams and businesses. By mimicking its installer, attackers increase their chances of tricking victims into downloading the fake version.
The use of poisoned Windows search results ensures the fake installer appears alongside legitimate software links, further boosting credibility. This tactic shows how attackers weaponize user trust in both search engines and common enterprise tools.
ClickFix: Still Effective
While ClickFix is not a new technique, its simplicity makes it enduring. Many users remain unaware of the risks of pasting commands into system utilities. By combining ClickFix with a fake AnyDesk installer, attackers created a layered deception that lowers suspicion.
“This is social engineering at its most effective,” Huntress researchers said. “The attackers combined familiarity, urgency, and trust in a legitimate brand to drive execution of malicious code.”
Huntress Findings
Huntress confirmed that multiple victims reported infections after downloading the fake AnyDesk installer. The researchers observed infrastructure linked to the campaign rotating domains, suggesting active efforts to evade takedown.
They also warned that while the current payload is MetaStealer, the same delivery method could be repurposed for ransomware or other malware families in future campaigns.
How to Protect Yourself
Experts recommend users and enterprises take the following precautions:
- Download software only from official vendor websites.
- Avoid copying and pasting commands from unverified sources.
- Use endpoint protection capable of blocking malicious command execution.
- Monitor Windows search results for malicious ads and report suspicious links.
- Train employees on ClickFix-style scams to reduce the likelihood of human error.
The AnyDesk MetaStealer campaign demonstrates how attackers continue to evolve ClickFix scams into practical delivery methods for modern malware. By blending poisoned search results, fake installers, and social engineering, adversaries exploit both user trust and system utilities.
For individuals, the attack shows how searching for a trusted app can lead directly to compromise. For organizations, it highlights the need to monitor software download practices and enforce stricter controls on command execution.
As Huntress researchers warned, the campaign may only be the beginning. The infrastructure used to spread MetaStealer could be weaponized for more destructive payloads in future operations.





