Salesloft has confirmed that its GitHub account was the initial entry point in the supply chain breach tied to its Drift application, an incident that has already impacted at least 22 companies. The campaign has been attributed to UNC6395, the same threat actor linked to recent high-profile cloud and SaaS attacks.
How the Breach Began
According to Salesloft’s updated advisory, attackers gained access to its GitHub account between March and June 2025. With this access, the threat actor was able to:
- Download content from multiple repositories
- Add a guest user to extend access
- Establish malicious workflows inside the environment
This foothold provided a launchpad for further activity, including infiltration of the Drift application environment integrated with Salesforce at many customer organizations.
Reconnaissance in Drift and Salesloft Environments
The investigation, conducted by Google-owned Mandiant, revealed that UNC6395 carried out reconnaissance inside both Salesloft and Drift environments. The activity included mapping repositories and testing access, but Salesloft emphasized that no evidence of data manipulation or destructive activity was found beyond reconnaissance.
Still, the breach exposed customer integrations to potential abuse, particularly through OAuth tokens and workflows linked to Salesforce and other SaaS platforms.
Impact Across 22 Companies
So far, 22 organizations have confirmed exposure linked to the Salesloft Drift breach. Customer support data, integration details, and account metadata were among the types of information potentially accessed.
Because Drift is commonly used as a chatbot for Salesforce-based support portals, attackers gained indirect access to sensitive customer interactions. While no payment or credential data has been confirmed stolen, researchers warn that exposed metadata could still aid in follow-up phishing or targeted campaigns.
The Role of UNC6395
UNC6395 has emerged as one of the most active threat groups exploiting identity-based attacks across major SaaS ecosystems. The group was previously linked to Google OAuth token abuse and other supply chain operations.
By starting with a GitHub compromise, UNC6395 leveraged the trust of open-source repositories and internal development workflows to pivot into connected SaaS applications. This attack chain highlights how developer platforms remain a critical weak point in modern supply chain security.
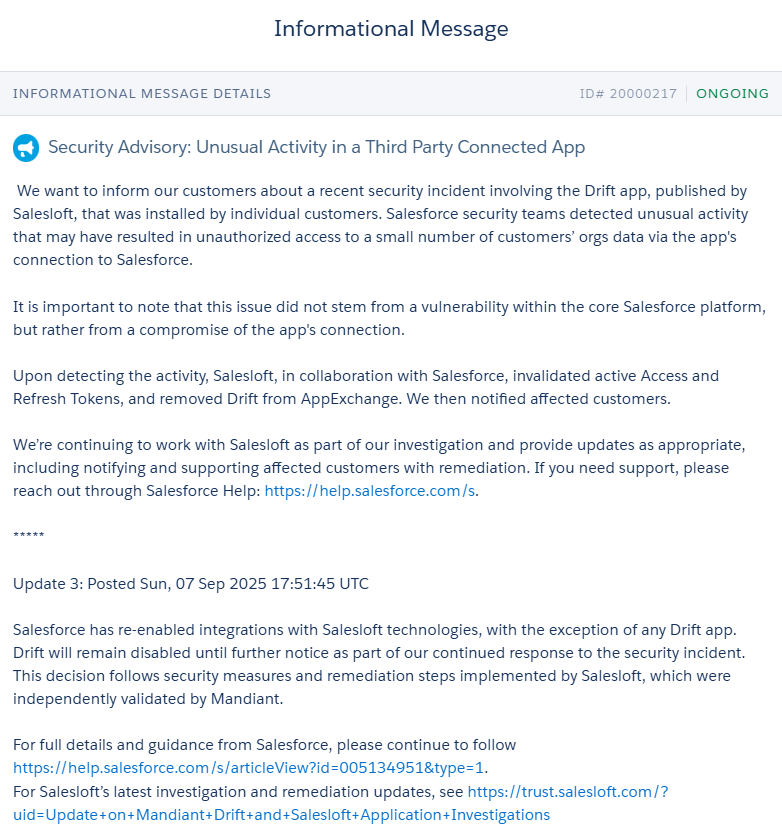
Screenshot of Security Advisory Message (Source: Salesforce)
Salesloft’s Response
Salesloft said it revoked unauthorized access, disabled compromised accounts, and worked with GitHub, Salesforce, and Mandiant to contain the incident. The company is now enhancing access controls, tightening third-party integrations, and rolling out expanded logging to detect suspicious behavior earlier.
In its advisory, Salesloft stated:
“With this access, the threat actor was able to download content from multiple repositories, add a guest user, and establish workflows. We have taken corrective actions to secure our systems and continue to work closely with impacted customers.”
The Salesloft GitHub compromise demonstrates how attackers can start small—with a single compromised account—and scale their reach into enterprise SaaS ecosystems used by dozens of organizations.
For the 22 confirmed victims, the immediate risks center on targeted phishing and metadata exposure. For the industry, the case illustrates how supply chain attacks continue to shift toward identity abuse, workflow manipulation, and third-party integrations, challenging traditional perimeter-based defenses.