Luxury fashion giants Gucci, Balenciaga, and Alexander McQueen have confirmed a data breach after their parent company, Kering, was targeted by the hacker group ShinyHunters. The incident exposed customer data and raises concerns over scams and targeted phishing campaigns against high-value clients.
How the Breach Happened
According to Kering’s disclosure, attackers infiltrated its systems in April 2025, though the breach went undetected until June 2025. By then, ShinyHunters claimed responsibility for exfiltrating sensitive customer information from the Paris-based luxury conglomerate.
The stolen data includes:
- Customer names and email addresses
- Purchase histories and order details
- Potentially billing and shipping information
Kering confirmed that no financial details such as credit card numbers were directly exposed, but warned that compromised data could still be exploited in phishing and impersonation campaigns.
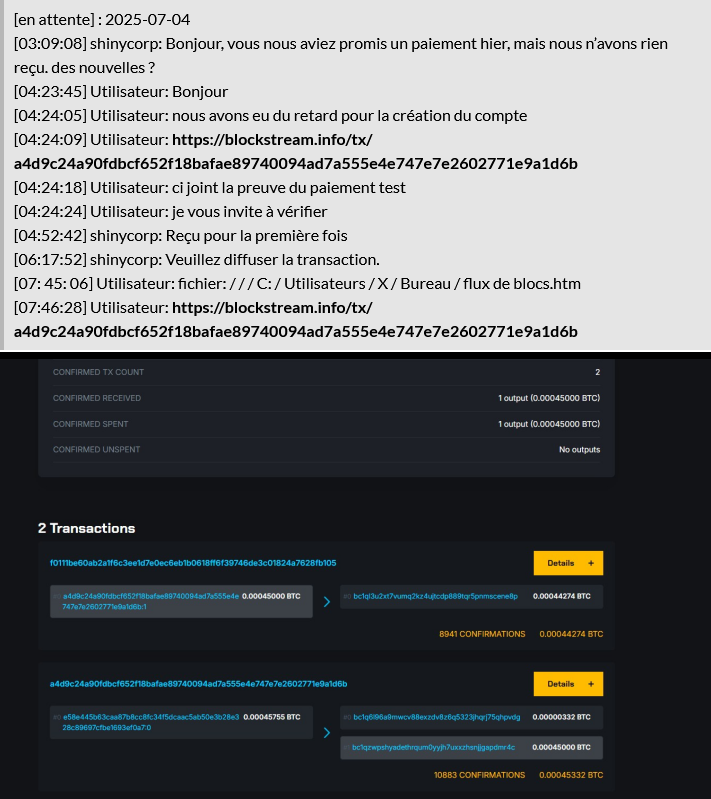
Alleged negotiation chatlog (Source: DataBreaches.net)
The Brands Impacted
Kering owns several of the world’s most prestigious fashion houses, including Gucci, Balenciaga, and Alexander McQueen. Customers of these brands often fall into affluent demographics, making them attractive targets for fraudsters seeking to exploit stolen data.
Security experts noted that the exposure of purchase histories could allow attackers to craft highly personalized spear-phishing emails, referencing specific luxury items or transactions to build credibility.
ShinyHunters’ Track Record
The ShinyHunters group has a long history of high-profile breaches and data leaks, often targeting companies with valuable customer datasets. The group is known for:
- Breaches of Tokopedia, Wattpad, and Microsoft GitHub repos in past years
- Selling stolen data on underground forums
- Publicizing attacks to pressure victims into ransom negotiations
Their involvement in the Kering breach suggests the incident was financially motivated, with stolen data potentially being sold on dark web marketplaces.
Kering’s Response
Kering confirmed the breach in a statement, saying it has notified data protection authorities and directly contacted affected customers via email. The company is working with cybersecurity experts to contain the breach and strengthen defenses.
“We take this incident seriously and regret the inconvenience caused to our customers. We are implementing enhanced monitoring and response measures to safeguard data in the future,”
Risks to Customers
Even though financial data was not directly compromised, exposed personal details can still fuel fraud and identity-related scams. Customers are at risk of:
- Phishing emails impersonating Gucci, Balenciaga, or Alexander McQueen support
- Fake invoices or order confirmations designed to steal payment details
- Spear-phishing campaigns that leverage past purchase information
Security experts recommend that customers remain cautious, verify all brand-related emails, and avoid clicking suspicious links.
The Kering data breach highlights the increasing focus of threat actors on luxury fashion brands, whose customer bases represent lucrative targets for cybercrime. For Kering, the incident is not only a regulatory and reputational challenge but also a reminder that cybersecurity is now a frontline issue for luxury retail.
For customers, the breach demonstrates that wealth and brand loyalty also make them potential targets for cybercriminals. Awareness and vigilance remain critical.





