Gunra ransomware has drawn the attention of cybersecurity researchers for its alarming resemblance to Conti, a now-defunct ransomware-as-a-service (RaaS) operation dismantled in 2022. Experts believe Gunra’s developers may be repurposing Conti’s leaked codebase, long circulated across cybercrime forums.
Its behavior—automated encryption, shadow copy deletion, and nearly identical ransom notes—mirrors Conti’s aggressive style. Once deployed, Gunra rapidly disables security defenses and locks down systems, leaving victims with few options for recovery.
The Rise of Gunra Ransomware
First detected in April 2025 by researchers at CYFIRMA, Gunra ransomware quickly gained traction. Early attacks were recorded across Japan, Egypt, Panama, Italy, Argentina, and the UAE, showing the malware’s global ambition. Victims ranged from real estate and healthcare to beverage distribution companies, indicating no specific industry focus.
Gunra is written in C/C++ and appends the “.ENCRT” extension to encrypted files. It leaves behind a ransom note titled “R3ADM3.txt,” which informs victims of stolen and encrypted data, then redirects them to a Tor-based portal for negotiations. Its foundation on Conti’s framework strengthens both stealth and impact—especially against vulnerable Windows systems.
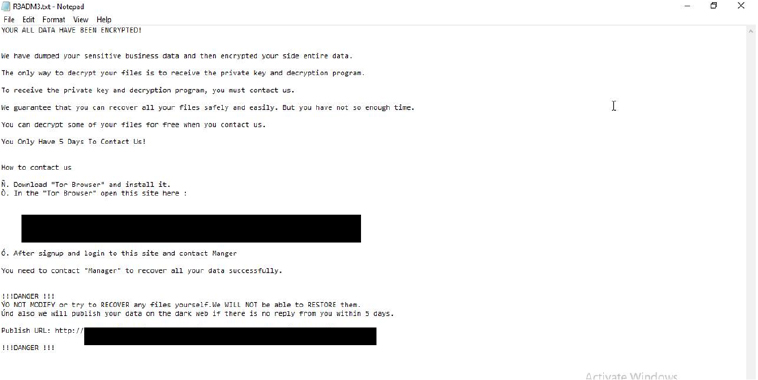
Gunra ransomware’s text file – “R3ADM3.txt” (Source: cyfirma.com)
Evasive Techniques and Extortion Tactics
Gunra ransomware uses a familiar double-extortion model: data is encrypted and exfiltrated, with victims threatened by public leaks if they fail to pay within five days. Negotiations take place on Tor portals styled like chat platforms, with attackers using titles like “Manager” to conduct ransom talks. These tactics have already affected manufacturing and healthcare sectors, where downtime is especially costly.
To cement control, Gunra removes Volume Shadow Copies using Windows Management Instrumentation (WMI), preventing data restoration. Obfuscation and anti-debugging techniques, such as the IsDebuggerPresent API, help it avoid detection. Reconnaissance is also built in—it maps out processes and system info before customizing its attack. AhnLab’s July 25, 2025 report warns that these techniques allow the malware to strike with surgical precision.
Global Spread and Sector Disruption
Gunra’s impact has crossed borders and sectors. In manufacturing, it has caused supply chain breakdowns. Healthcare systems have seen patient data exposed. Real estate firms and tech companies have lost access to sensitive documents and proprietary assets. According to Intertec Systems, over 11 high-profile organizations have been compromised since the malware surfaced.
Rewterz documented attacks on six continents by early June 2025. These events emphasize the borderless nature of ransomware and the importance of international coordination to track and respond to threat actors like Gunra.
Files encrypted by this ransomware (Source: cyfirma.com)
Ransomware Trends and Gunra’s Growing Influence
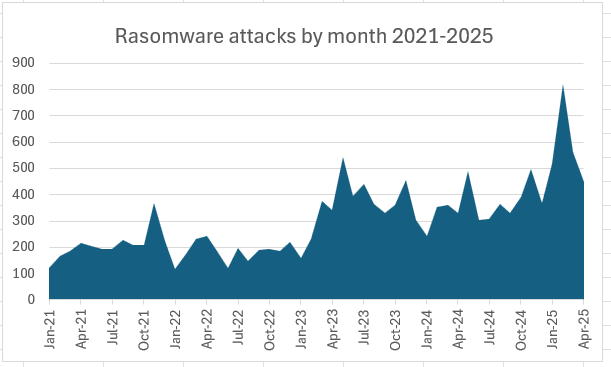
The broader ransomware landscape in 2025 is increasingly volatile. While Qilin led in volume with 81 reported attacks in April, new groups like Silent, Crypto24, Bert, and Gunra are quickly rising. Cyble’s research shows a sharp resurgence in ransomware activity—470 victims in April alone—despite a brief decline in 2022.
Gunra’s tactics place it among the most dangerous of these emerging threats. Like its peers, it prioritizes high-value targets. AAG IT Support reports that manufacturing remains the top sector hit, followed by IT. The U.S. alone accounted for 47% of all ransomware attacks in mid-2025. Meanwhile, SOC Prime notes that average recovery costs ballooned to $2.73 million in 2024—an increase of over 500% from the prior year. Attacks like Gunra’s are driving that figure higher.
Mitigating the Risk of Gunra Ransomware
Gunra ransomware represents a turning point in today’s threat environment. With its Conti-inspired structure and double-extortion pressure, it has quickly become a global menace. Its ability to cripple organizations across sectors underlines the need for stronger, more proactive defense strategies.
Enterprises must treat threat intelligence as a front-line tool. Defensive tactics such as endpoint detection and response (EDR), segmented networks, and rigorous employee awareness training are now vital. Gunra and other latest ransomware attacks will continue to evolve, but with informed preparation, their damage can be contained.





