Microsoft Threat Intelligence has uncovered a new phishing campaign that hides malicious code in SVG files and appears to use AI-powered techniques to evade detection. The attack, spotted on August 18, 2025, targeted U.S.-based organizations and relied on compromised small business email accounts to deliver fraudulent file-sharing messages.
How the Campaign Worked
The attack began with emails masquerading as file-sharing requests. The messages were sent from legitimate but compromised email accounts, giving them credibility. The attachment appeared as a 23MB file labeled “PDF – 6 pages”, but the actual file extension was .svg (Scalable Vector Graphic).
While SVG files are commonly used for graphics, they can also embed dynamic and interactive code. In this case, the malicious SVG contained obfuscated scripts capable of redirecting victims to credential-harvesting sites.
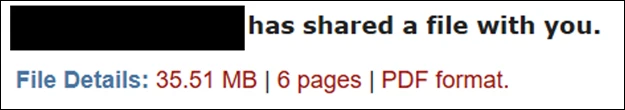
Phishing email example (Source: Microsoft)
Because the file disguised itself as a PDF and came from a trusted sender, victims had little reason to suspect it was malicious.
The Role of AI
Microsoft researchers noted that the complexity of the embedded code suggested attackers may have used Large Language Models (LLMs) to generate or enhance it. LLMs, the same technology behind chatbots, can produce cleaner, less error-prone code than many human-written phishing scripts.
By using AI to automate obfuscation, attackers increase their chances of bypassing signature-based detection systems. This marks a shift from crude phishing kits toward AI-assisted campaigns that look more professional and are harder to catch.
Why SVG Files Are Dangerous
Unlike traditional attachments, SVG files don’t always trigger security alerts because they are commonly considered safe image files. However, they can hide JavaScript or other code that executes when opened in a browser or certain applications.
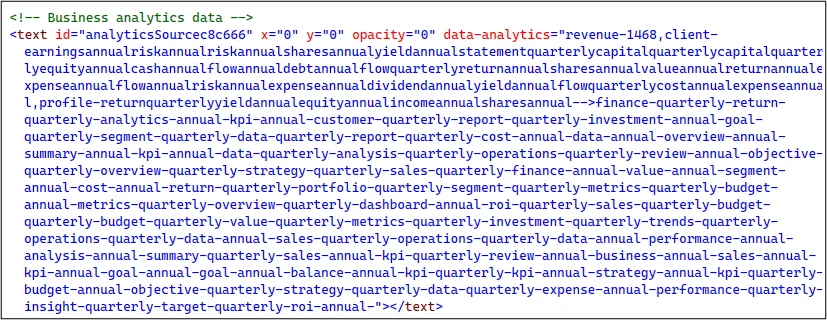
Sequence of business-related terms (Source: Microsoft)
This makes SVGs particularly dangerous in phishing scenarios:
- They look harmless to users.
- They bypass some email security filters.
- They allow dynamic redirection to attacker-controlled sites.
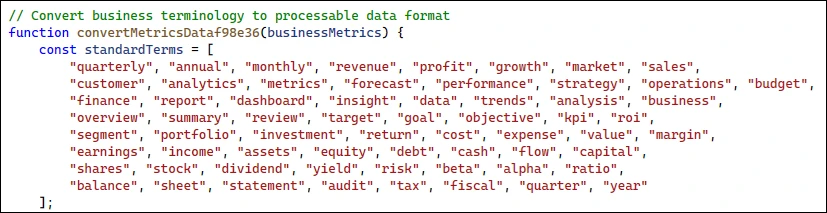
Conversion of business terminology to processable malicious code (Source: Microsoft)
Microsoft’s Response
Microsoft Threat Intelligence blocked the campaign before it could spread widely, but the discovery highlights an emerging trend of AI-enhanced phishing. The company said it is monitoring for further activity linked to the same infrastructure and has shared indicators of compromise (IOCs) with partners.
The phishing campaign appears limited in scale, but its sophisticated use of AI and obfuscated SVG payloads demonstrates how attackers are evolving beyond traditional methods.
Expert Concerns
Security experts warn that this campaign may represent the start of a broader wave of AI-driven phishing. By using LLMs to refine malicious code, attackers can rapidly adapt, reducing the chances of detection and boosting success rates.
“AI makes phishing campaigns scalable and cleaner,” one analyst noted. “The days of spotting scams based on poor grammar or sloppy coding are disappearing.”
Protecting Against AI Phishing
Organizations can take several steps to defend against attacks like this:
- Educate employees on verifying file extensions, especially disguised formats like
.svg. - Configure email security tools to scan inside SVG attachments.
- Enforce multi-factor authentication (MFA) to reduce the impact of stolen credentials.
- Monitor for abnormal login attempts from unfamiliar locations or devices.
- Deploy advanced threat detection systems that analyze behavior, not just file types.
For individuals, the key takeaway is to be cautious with unexpected file-sharing emails, even if they come from familiar contacts.
The SVG phishing campaign flagged by Microsoft underscores the convergence of AI and traditional cybercrime. By embedding malicious scripts in trusted file types and using AI to refine obfuscation, attackers are creating a new generation of phishing attacks that are harder to detect and more likely to succeed.
As this technique matures, enterprises should expect more phishing attempts that combine legitimate-looking delivery, AI-generated payloads, and uncommon file formats. Defenses must evolve quickly to keep pace.





