Cybersecurity researchers at FortiGuard Labs have discovered a new malware threat called MostereRAT, which is being spread through phishing campaigns targeting Windows devices. Classified as high severity, this Remote Access Trojan (RAT) provides attackers with full control of compromised systems using tools like AnyDesk and TightVNC.
How the Malware Works
MostereRAT begins with phishing emails carrying malicious attachments or links. Once executed, the malware establishes persistence on the victim’s Windows machine and disables basic security protections.
The RAT then downloads and installs legitimate remote access tools — namely AnyDesk and TightVNC — but configures them for attacker-controlled sessions. By piggybacking on these trusted applications, MostereRAT ensures that remote activity looks less suspicious in network logs.
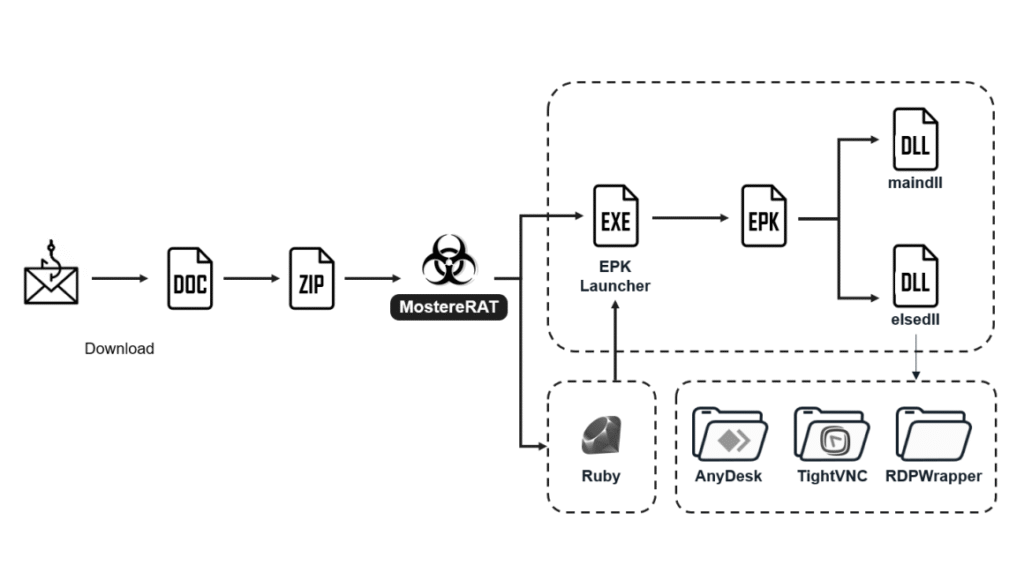
Attack Flow (Source: fortinet.com)
Capabilities of MostereRAT
FortiGuard Labs reported that MostereRAT enables attackers to:
- Gain full desktop control of infected Windows devices
- Steal files, credentials, and stored browser data
- Monitor keystrokes and screen activity
- Move laterally within enterprise networks
- Deploy additional payloads, including ransomware or infostealers
This dual use of remote access tools and RAT functionality makes detection challenging. The malware blends malicious behavior with legitimate application traffic.
Why AnyDesk and TightVNC Are Abused
Attackers increasingly weaponize legitimate remote desktop tools because they provide reliable connections, are commonly whitelisted in enterprises, and are less likely to trigger endpoint defenses.
By leveraging AnyDesk and TightVNC, MostereRAT operators gain stealthy persistence. Security teams may misinterpret sessions as authorized IT activity, allowing attackers to maintain long-term access without raising alarms.
Phishing Remains the Entry Point
The campaign underscores the continued effectiveness of phishing as an initial attack vector. Emails carrying MostereRAT are designed to appear urgent and business-related, enticing recipients to open attachments or click links that deliver the payload.
Researchers noted that the phishing emails mimic financial documents and internal notices, a tactic often used to target corporate employees.
FortiGuard’s Analysis
According to FortiGuard Labs, MostereRAT’s infrastructure uses dynamic DNS and proxy layers to obscure command-and-control servers. The malware also employs obfuscation techniques to avoid detection during analysis.
“MostereRAT demonstrates a dangerous convergence of malware and legitimate software,” FortiGuard warned. “By relying on AnyDesk and TightVNC, the attackers gain not only persistence but also a cloak of legitimacy.”
The MostereRAT Windows campaign illustrates how attackers continue to refine RAT operations by pairing malware with trusted remote access tools. By exploiting AnyDesk and TightVNC, adversaries make detection harder while gaining complete control of targeted systems.
For enterprises, this campaign highlights the urgent need to monitor legitimate software misuse alongside traditional malware signatures. For individuals, it reinforces the importance of phishing awareness as the first line of defense.





