The Node.js vulnerability CVE‑2025‑27210, disclosed on July 15, 2025, allows attackers to exploit Windows reserved device names (CON, PRN, AUX) to bypass path traversal protections and access sensitive files. This article unpacks the flaw, its real‑world consequences, and actionable mitigation guidance for developers and security teams.
A Deep Dive into the CVE‑2025‑27210 Node.js Vulnerability
On July 15, 2025, the Node.js Project released security updates addressing a critical issue: Windows Device Names bypass path traversal protection in path.normalize() and path.join() functions. Attackers can exploit reserved device names—such as CON, PRN, and AUX—mid‑path to evade sanitization checks and access files outside permitted directories. For example, a crafted path like ....\CON..\credentials.json could trick the runtime into exposing credential stores or configuration files intended to be off‑limits to the executing user.
How Path Normalization Falls Short
Under normal circumstances, path.normalize() and path.join() are used to resolve and sanitize file paths, removing traversal sequences like ../. However, on Windows systems these APIs treat strings like CON and PRN as special device names. The normalization logic fails to recognize device names mid‑path, effectively allowing traversal bypass. An attacker embedding a device name can obscure malicious paths from detection and gain unauthorized file access.
This flaw has serious implications for applications running on Windows hosts. If credential files, API tokens, SSH keys, or any sensitive resource resides in accessible directories, attackers might exploit this vulnerability to extract them and trade them on dark‑web markets. Shared hosting, CI pipelines, and developer environments face heightened risk. Such credential loss could facilitate lateral movement, privilege escalation, or complete system compromise.
Node.js Security Updates and Affected Versions
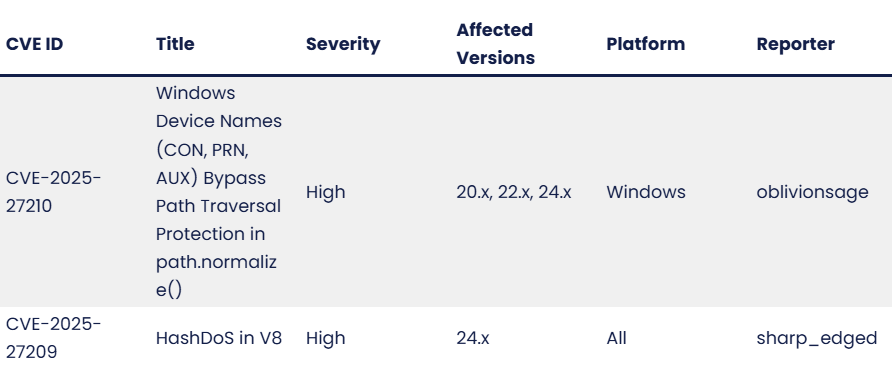
In response to CVE‑2025‑27210, Node.js released patched versions across major release lines on July 15, 2025:
These versions handle Windows reserved names properly, eliminating the traversal bypass.
The same updates also addressed HashDoS vulnerability CVE‑2025‑27209 in the V8 engine, which reintroduced Hash Collision Denial‑of‑Service risk. While not credential‑focused, it could degrade service availability on Node.js 24.x deployments.
(image via: GBHackers.com)
Mitigation Guidance for Developers
Developers and DevOps teams should:
- Upgrade immediately to patched versions: v20.19.4, v22.17.1, or v24.4.1.
- Audit all user‑supplied path handling, especially using
path.join()ornormalize(), ensuring input validation and sanitization. - Restrict file‑I/O to whitelisted directories, isolating sensitive resources.
- Containerize or sandbox file access, especially for Windows‑based services.
- Monitor file access logs for unexpected reads of device names or unauthorized paths.
These practices align with recommendations from CISA and experts at Bleeping Computer, emphasizing layered protection strategies.
CVE‑2025‑27210 joins a growing list of Node.js path‑handling flaws. A lesser-known vulnerability, CVE‑2025‑23084, previously attempted to address a similar device‑name issue but was incomplete. Meanwhile, other major malware campaigns like the BADBOX 2.0 botnet highlight the broader risks of unauthorized access and hidden system exploits—especially in environments where input control is weak.
In light of CVE‑2025‑27210, Windows‑based Node.js developers must act swiftly. Upgrading runtime versions and reinforcing path validation are essential safeguards against credential theft and system compromise.