An investigation on July 26, 2025 uncovered a widespread campaign involving fake GitHub repositories distributing malware strains such as RedLine and DeerStealer, designed to harvest cryptocurrency wallet credentials. The open source malware operation infiltrated developers and investors seeking blockchain tools—and leveraged open source software security gaps to propagate the malware. This incident raises significant questions around trust in repositories and GitHub security practices in environments where code is freely shared.
The Malware Campaign
Security researchers discovered dozens of impersonated GitHub repositories offering crypto wallet utilities. These repositories were crafted to appear legitimate, using names and descriptions similar to known open‑source tools. Downloads from these repos delivered executable payloads, which upon installation deployed malware like RedLine or DeerStealer. Once activated, the malware scanned local systems and browser storage for cryptocurrency wallet credentials, forwarding them to attacker‑controlled servers. The campaign’s emphasis on mimicking trusted repositories indicates a sophisticated exploitation of open source software security vulnerabilities.
RedLine and DeerStealer
Two variants dominated the campaign:
- RedLine Stealer: Known for harvesting browser-stored credentials, cookies, and cryptocurrency wallets. The malware runs silently and exfiltrates data via encrypted channels.
- DeerStealer: Specialized in extracting wallet files and credentials from desktop environments and browser extensions, using heuristics to target crypto directories.
Both malware families are built on scripting languages and modular architecture, enabling stealthy execution within environments that rely heavily on open‑source tooling.
Infiltration and Propagation Mechanics
Attackers posted code repositories with names such as “WalletManager‑CLI,” “CryptoBackupTool,” or “DecryptWallet,” often accompanied by README files claiming cross‑platform support. In several cases, the projects displayed legitimate-seeming commit history and activity logs to boost credibility. However, closer forensic analysis showed cloned commit messages and fabricated activity timestamps.
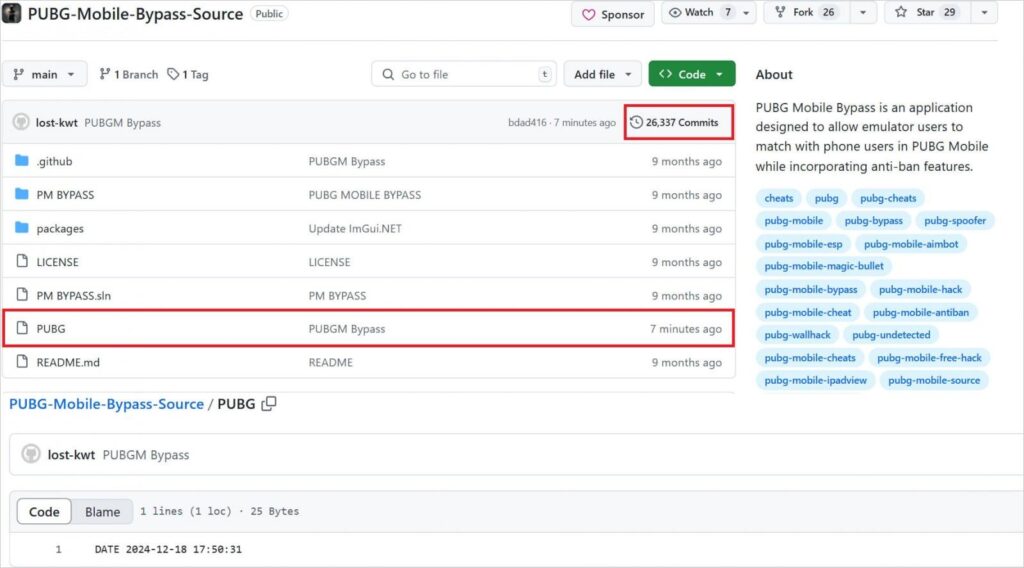
Malicious GitHub repositories (Source: Kaspersky.com)
Clone counts and star metrics were artificially inflated using bot accounts to simulate popularity. Investigators confirmed that no legitimate contributors were associated with these repositories; all pull requests were either fake or nonexistent.
Malicious GitHub repositories (Source: trendmicro.com)
Target Impact
This campaign particularly targeted crypto investors and developers who turn to GitHub for wallet utilities, token management scripts, or backup tools. Victims reported unexplained wallet drains and unauthorized transactions shortly after interacting with the malicious repos.
While project descriptions promised open‑source validation and transparent code review, the distributed binaries were obfuscated and unsigned. The malware bypassed common static detection tools by packing payloads that only decrypted at runtime, signaling the growing sophistication of open source malware threats.
GitHub Ecosystem
The episode calls into question assumptions about trustworthiness in public repositories. The prevalence of fake or lookalike repos undermines the credibility of GitHub security, especially for projects with blockchain users as a core audience. Risk increases when users download binary releases rather than building from source or verifying signatures.
The attack highlights a vital tension in the ecosystem: open collaboration invites innovation, but also opens avenues for open source software security compromise through impersonation and misdirection. Shadow projects optimized for crypto theft may continue proliferating unless detection and vetting mechanisms evolve.





