Google’s threat intelligence team dropped alarming details this week about a massive Scattered Spider attack campaign targeting VMware ESXi hypervisors across American corporate networks. The notorious cybercriminal group has been systematically launching ransomware attacks against retail chains, airlines, and insurance companies, using nothing more than smooth-talking phone calls to IT help desks.
What makes this campaign particularly nasty is how the attackers have perfected the art of sounding legitimate. These aren’t your typical broken-English scammers – the operators can mimic regional accents, drop company jargon like they’ve worked there for years, and maintain their cover even during lengthy conversations with suspicious IT staff.
The July 27 intelligence report paints a troubling picture of an adversary that’s evolved far beyond simple phishing emails. Microsoft researchers who’ve been tracking the same group under the designation UNC3944 say these criminals have become frighteningly good at psychological manipulation, often succeeding where sophisticated malware would fail.
Scattered Spider Attack Methods Target Hypervisor Infrastructure
The Scattered Spider attack playbook starts with reconnaissance that would make corporate spies jealous. Before making a single phone call, the group’s operators research their targets extensively, learning employee names, internal processes, and enough technical vocabulary to fool even experienced IT professionals.
When they finally dial those help desk numbers, the conversations sound perfectly routine. A “stressed employee” needs their password reset because they’re locked out before an important client meeting. Maybe someone from the “regional office” needs urgent access to fix a system that’s “causing issues for customers.” The scenarios vary, but the underlying deception remains brutally effective.
Once they talk their way past the first line of defense, these attack teams move with startling speed. Security researchers have documented cases where the group gained complete control over vSphere environments within hours of that initial phone call. They’re not fumbling around trying to figure out the infrastructure – they know exactly what deployment strategy they’re after.
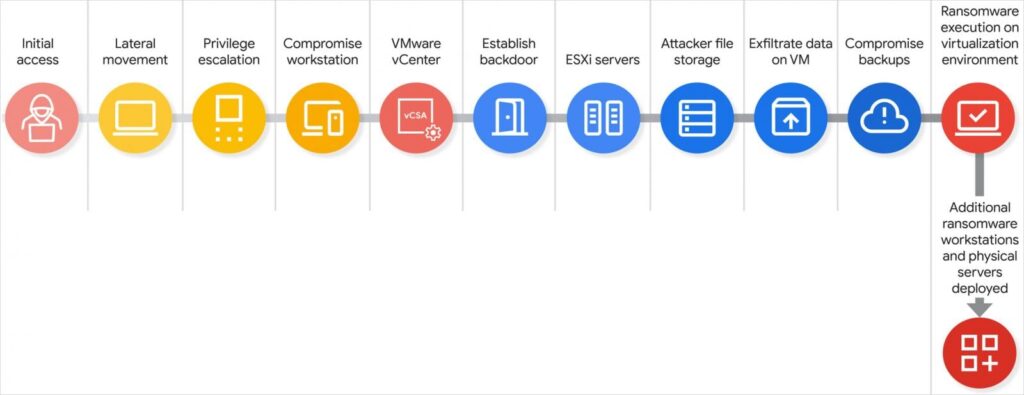
Spider attack chain (Source: Google)
The technical execution that follows shows just how far this group has come. They’ll enable SSH on compromised ESXi hosts, reset root passwords, and essentially own the entire virtualized backbone of their target company. When you control the hypervisor, you control everything running on top of it, making these attacks incredibly effective.
Ransomware Attacks Devastate Critical Business Operations
The beauty of targeting hypervisors, from a criminal’s perspective, is the massive bang for their buck in these ransomware attacks. Instead of infecting individual computers one by one, each Scattered Spider attack can paralyze hundreds of virtual machines with a single ransomware deployment on the ESXi host.
The sectors they’re hitting with these ransomware attacks aren’t random either. Retail operations grinding to a halt during peak shopping periods. Airlines unable to process bookings or manage flights. Insurance companies locked out of critical claims processing systems. These aren’t just IT problems – they’re business catastrophes that executives notice immediately when ransomware strikes.
Google’s analysis shows the group has gotten smart about timing their ransomware attacks too. They’re not just deploying ransomware and hoping for the best. The attackers spend time inside networks, mapping out the most critical systems and waiting for moments when downtime will cause maximum pain during their Scattered Spider attack campaigns.
What’s particularly concerning is how traditional security tools often miss hypervisor-level ransomware attacks entirely. Most endpoint protection software sits on individual virtual machines, completely blind to what’s happening at the ESXi layer where these devastating ransomware attacks unfold.
Social Engineering Powers Modern Ransomware Attacks
The most unsettling part of this whole situation is watching expensive security programs crumble against old-fashioned social engineering tactics used in these Scattered Spider attack campaigns. Companies spend fortunes on next-generation firewalls, AI-powered threat detection, and zero-trust architectures, only to get owned by ransomware attacks launched through someone with a phone and good acting skills.
CrowdStrike’s incident response teams have seen this pattern repeatedly throughout 2025. Organizations with mature security programs, dedicated SOCs, and comprehensive employee training still fall victim to these carefully crafted Scattered Spider attack campaigns that lead to crippling ransomware infections.
The psychological tactics have become increasingly sophisticated. The criminals behind these ransomware attacks don’t just impersonate employees – they create believable backstories, reference recent company events, and even know enough about internal politics to make casual small talk that builds trust with their targets.
Silent Push researchers have documented successful Scattered Spider attack incidents at household names like Credit Karma and Forbes, proving that brand recognition and security maturity offer little protection against skilled social engineers who’ve perfected their ransomware attack methodologies.
Critical Infrastructure Faces Escalating Ransomware Attacks
The scale of this Scattered Spider attack campaign suggests the group has grown from a loose collection of cybercriminals into something resembling an organized criminal enterprise. The systematic targeting of U.S. critical infrastructure sectors with these coordinated ransomware attacks indicates planning and coordination that goes well beyond opportunistic strikes.
Aviation companies have been hit particularly hard by these ransomware attacks, with some incidents affecting flight operations and passenger services. The insurance sector has faced similar disruptions from ransomware, with claims processing systems compromised during periods of high activity following natural disasters.
The retail attacks have coincided with major shopping events, suggesting the group times their ransomware attacks for maximum impact and leverage during ransom negotiations. This level of strategic thinking demonstrates an evolution in cybercriminal operations that security professionals are still struggling to counter effectively.
The continuing success of these Scattered Spider attack campaigns against well-defended targets highlights a fundamental weakness in how organizations approach cybersecurity, where human factors often prove more vulnerable than technical systems when facing sophisticated ransomware attacks targeting critical infrastructure.





