On July 27, 2025, researchers uncovered Soco404, a stealthy crypto mining malware abusing AWS and Azure misconfigurations to hijack cloud resources. By embedding malicious scripts in fake 404 error pages, the Soco404 crypto miner quietly mines Monero using stolen computing power. This campaign adds to the growing wave of crypto mining malware, highlighting a key trend in cyber threats of 2025 and the increasing need for stronger cloud defenses.
Cloud Exploits and Global Spread of Soco404 Malware
First identified by Wiz Research on July 23 and confirmed by Aqua Security days later, the Soco404 crypto miner targets poorly secured cloud services. It focuses on exposed PostgreSQL databases and vulnerabilities like CVE-2025-24813 in Apache Tomcat.
Victims span sectors including manufacturing, healthcare, and tech, with incidents reported in Japan, Egypt, and the UAE. By hiding its payload in fake 404 error pages, Soco404 evades traditional defenses, reinforcing its threat status in cloud environments and among top cyber threats in 2025.
Operational Disruption and Financial Impact of Soco404
Soco404 drains resources silently, inflating cloud bills and degrading system performance. Blockchain firms are especially vulnerable, where delayed smart contract execution can stall operations.
Intertec Systems reports over 11 major organizations hit since April 2025. Because the malware often runs unnoticed, costs escalate quickly. Healthcare systems face added risk with potential data exposure. As crypto mining malware evolves, its hidden toll on infrastructure becomes harder to ignore.
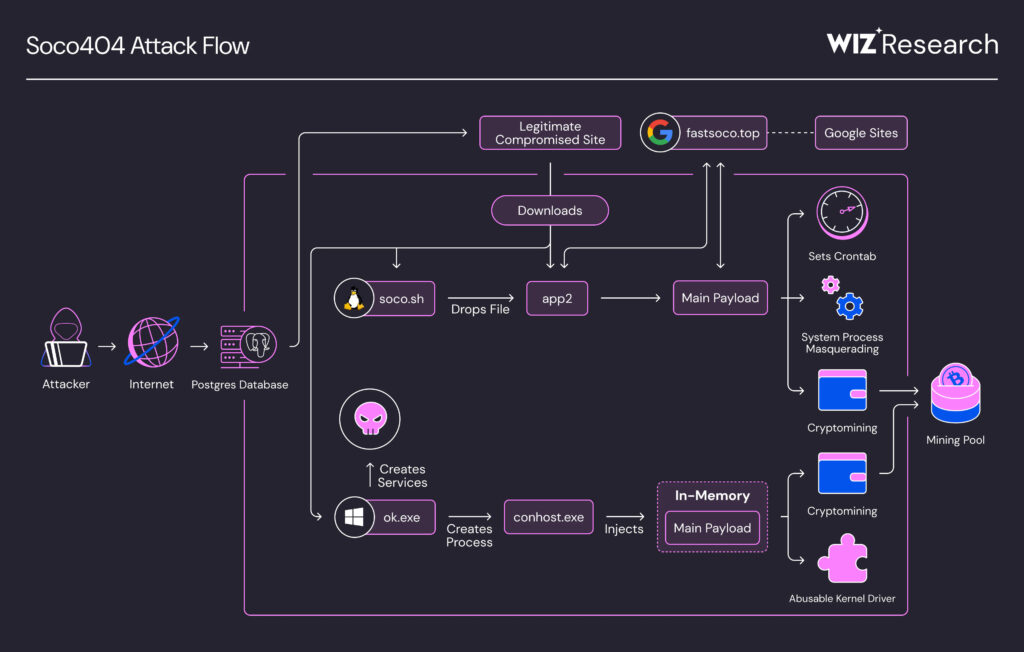
Attack flow (Source: wiz.io)
Expert Analysis Reveals Growing Cloud-Based Threat Pattern
Wiz researchers Maor Dokhanian and Shahar Dorfman view Soco404 as part of a broader scam network. Aqua Security draws parallels to Koske, another crypto mining malware that spreads via tainted container images—a growing tactic in cloud-focused cyber threats.
While AWS and Azure haven’t directly addressed Soco404, Wiz emphasizes the importance of regular configuration audits and usage monitoring. As cyber threats in 2025 accelerate, experts warn that cloud platforms remain high-priority targets requiring constant vigilance.
Soco404 Crypto Mining Malware
Soco404 operates across Linux and Windows, deploying platform-specific payloads written in C/C++. It delivers its code through fake 404 error pages, previously hosted on services like Google Sites before takedown.
It exploits vulnerabilities like CVE-2025-24813 and open PostgreSQL instances. Wiz estimates nearly one-third of self-hosted setups remain exposed.
To stay persistent, Soco404 modifies cron jobs and .bashrc files drawing comparisons to other cross-platform malware like Chaos RAT on Linux. On Windows, it uses certutil and PowerShell to install the WinRing0.sys driver, gain admin privileges, and disable logging—making detection much harder for defenders.
Why Soco404 Signals a Shift in 2025 Cyber Threats
Soco404 reflects the evolution of cloud-targeted malware. Its creative use of 404 pages to mask attacks shows how adaptable modern threat actors have become. Even brief system compromise can disrupt blockchain platforms and decentralized services as seen in other infrastructure-targeted crypto attacks.
With over 40,000 CVEs logged in 2024 and more expected this year, the cloud’s expanding attack surface demands proactive defense. Soco404 is a warning sign in a growing pattern of advanced crypto mining malware and 2025’s evolving cyber threat landscape.
Organizations must strengthen cloud security to block threats like Soco404. Regularly audit AWS and Azure settings—especially PostgreSQL permissions—and close any misconfigured services.
Use multi-factor authentication, enforce strong credentials, and follow least-privilege principles to limit attack vectors. Monitor system behavior with tools like AWS CloudTrail and Azure Monitor to catch abnormal resource usage.
Patching key vulnerabilities like CVE-2025-24813 is essential. Keeping pace with evolving cyber threats in 2025 means leveraging real-time intelligence from groups like Wiz as new campaigns surface and adapt.





