The SS7 surveillance attack, disclosed on July 19, 2025, involves a covert tracking method used by a surveillance vendor exploiting flaws in the Signaling System No. 7 (SS7) protocol. This exploit enables attackers to pinpoint mobile phone locations without telecom or user consent. This article details the technical mechanics of the vulnerability, its implications for mobile privacy, and practical recommendations to help users mitigate risk.
How the SS7 Surveillance Attack Works
The SS7 signaling protocol, essential for global mobile communications, contains inherent vulnerabilities in its authentication and routing mechanisms. In the July disclosure, analysts showed that a vendor used compromised SS7 routing tables to send “Location Request” messages that mobile network operators responded to automatically. These requests exploit SS7’s implicit trust model—networks inherently accept and process messages from other networks without verifying their legitimacy.
Exploiting this trust, the attacker’s surveillance system bypasses user consent and telecom security layers. The Location Request returns precise latitude and longitude data for a target handset. Affected operators included both legacy and modern LTE networks, indicating that SS7 vulnerabilities persist across infrastructure upgrades. This flaw contrasts with SIM-based attacks that require physical or near-field access; instead, the SS7 surveillance attack operates entirely over the network backend.
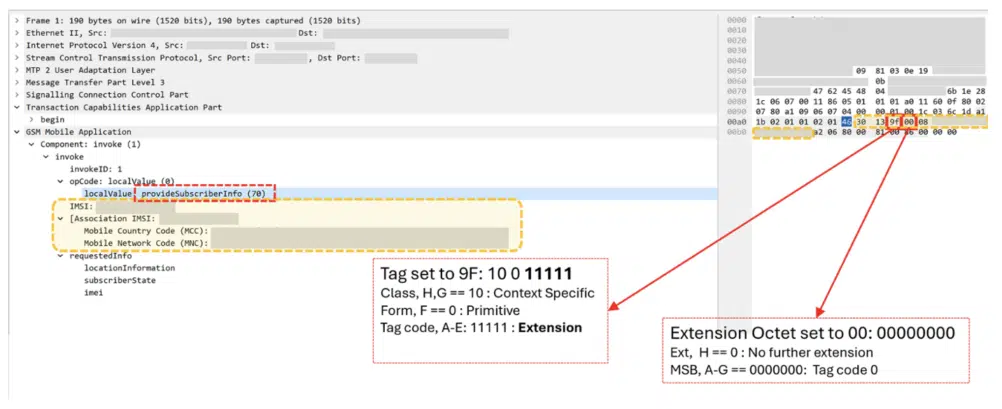
Attack Message (via GBHackers.com)
Importantly, this method does not require malicious software installed on the victim’s device. No interaction, phishing, or user permission is necessary. Operators often do not log these location requests as critical events, as the messages appear as routine network management traffic. Researchers suggest that hundreds of millions of location requests have been made over the past year, largely unnoticed by carriers or regulators.
Privacy and Security Implications for Users
The implications of the SS7 surveillance attack reach beyond personal privacy. Unauthorized tracking of mobile devices grants threat actors detailed movement histories and real-time location data. Individuals at higher risk include journalists, activists, executives, or individuals under domestic threats. Compromised data can also facilitate physical surveillance or stalking without leaving a trail on the target’s device.
The attack intensifies threats to mobile wallets, two-factor authentication relying on SMS, and location-based services. Adversaries might coordinate social engineering or physical impersonation based on captured location data—similar to tactics seen in the Node.js credential exposure vulnerability where attackers exploited system-level trust to bypass safeguards. Given that many users assume telecommunication networks protect against such intrusions, the SS7 vulnerability shatters this trust model. The persistent exploitation by a surveillance vendor indicates that these attacks are not theoretical—they are active, ongoing threats.
Network-level logging and anomaly detection tools remain inadequate for detecting SS7-based surveillance. Many operators treat SS7 as legacy infrastructure and do not apply modern cybersecurity controls. Aggregated location request logs could expose malicious behaviors, yet few operators in 2025 have implemented such measures across their infrastructure.
Telecom Industry Response and Defense Measures
Following the July 19 report, several mobile network operators released advisories acknowledging potential SS7 vulnerabilities. Some providers have begun deploying Signaling Firewall solutions that filter suspicious Location Request patterns. Still, implementation remains inconsistent across regions and operators.
Critically, these firewalls must identify and block unauthorized SS7 messages while preserving legitimate traffic. Vendors offering signaling firewall solutions, such as AdaptiveMobile or Nokia, recommend operators configure geolocation services to respond selectively—based only on specific request types and source validation. While these measures improve resilience, they cannot fully remediate SS7’s protocol-level flaws, which require global coordination and industry-wide changes to trust relationships within SS7 routing.
Steps for Privacy-Conscious Mobile Users
Although users cannot change telecom infrastructure directly, several strategies reduce exposure to SS7 surveillance attacks. First, disabling location-tracking features and limiting app permissions prevent OS-level misuse, but do not stop network-based requests. Second, employing encrypted communication apps that do not rely on network-originated messages for two-factor authentication can reduce risk exposure even if location data is indirectly used for phishing.
Advanced users might consider using eSIMs from operators with demonstrated SS7 protections or deploying burner devices for sensitive communications. Privacy-focused VPNs or Secure Network Access configurations on mobile devices could provide partial obfuscation, though they do not hide physical location from the cellular network. Critics warn these strategies offer imperfect coverage—but they create additional barriers for opportunistic surveillance.
The SS7 surveillance attack illustrates how foundational telecom weaknesses persist decades into modern mobile usage. By enabling real-time phone tracking without user consent, this vulnerability opens avenues for abuse, stalking, and political suppression. Users, privacy advocates, and operators must pursue multi-layered defenses: deploying network firewalls, regulatory monitoring, infrastructure modernization, and informed device use. Vigilance remains essential as the telecommunications landscape evolves and threat actors adapt.