Security researchers have uncovered a large-scale malware campaign distributing an infostealer dubbed TamperedChef through fake PDF editing applications. The campaign relied on Google ads to drive victims to fraudulent websites hosting malicious downloads, blending legitimate branding with carefully timed activation of hidden payloads.
How the Campaign Works
According to researchers, the attackers built multiple websites that promoted seemingly legitimate PDF editor tools. When users clicked on the sponsored Google ads, they were redirected to domains hosting trojanized installers. These apps were signed with fraudulent certificates from at least four different companies, adding credibility and bypassing some security checks.
The fraudulent apps operated with a two-phase approach. Initially, they behaved like functioning PDF tools to avoid suspicion. After a delay, they activated the TamperedChef infostealer, which harvested sensitive data from infected systems.
Stolen information included:
- Browser cookies and stored credentials
- Autofill data (emails, phone numbers, addresses)
- Cryptocurrency wallet details
- Authentication tokens for SaaS platforms
- A Multi-App Ecosystem
Researchers discovered that TamperedChef was not the only payload. The operators designed the apps to download each other, creating a modular malware ecosystem. Some variants enrolled compromised machines into residential proxy networks, monetizing infected systems by reselling bandwidth.
In total, more than 50 domains were identified hosting these fraudulent apps. This scale indicates significant planning and infrastructure investment. The coordinated nature of the operation suggests a well-resourced threat actor.
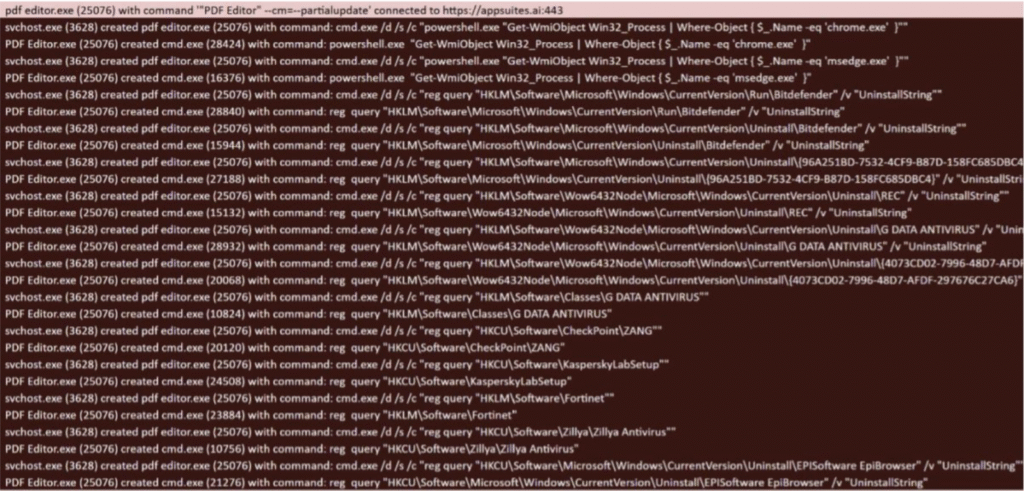
TamperedChef infostealer checking for security agents (Source: Truesec)
Timing as an Evasion Technique
One striking detail was the campaign’s patience. The attackers waited for the Google ads to run their course before triggering the malicious components inside the applications. This tactic ensured the apps gained traction and avoided early takedowns by appearing safe during initial scrutiny.
Once the ad campaigns delivered enough installs, the operators flipped the switch to activate the infostealer functions. Security experts believe this delayed activation was key to bypassing both automated ad review systems and initial malware analysis.
Infostealers remain one of the fastest-growing categories of malware, with underground marketplaces thriving on stolen credentials. TamperedChef fits this trend by collecting valuable login data, browser tokens, and crypto wallet information at scale.
By using Google ads as the distribution vector, the attackers exploited user trust in a widely used platform. Unlike phishing emails, malvertising campaigns can cast a wide net, targeting both consumers and professionals searching for common tools like PDF editors.
Response from Researchers
Analysts have reported the fraudulent domains and certificates to Google and other security vendors. Several takedowns are underway, but given the scale—over 50 identified domains—researchers expect the operators will pivot quickly with new infrastructure.
Users who downloaded PDF tools from ads in recent weeks are advised to:
- Uninstall suspicious applications.
- Run full endpoint scans for malware.
- Rotate all passwords, especially for financial or work accounts.
- Monitor for unusual account activity or login attempts.
The TamperedChef infostealer campaign demonstrates how cybercriminals continue to refine malvertising strategies. By combining fraudulent certificates, convincing branding, and timed payload activation, attackers created a sophisticated funnel to deliver spyware at scale.
Experts warn that malvertising-driven malware will likely become more common, especially as platforms like Google ads remain lucrative entry points. The case also highlights the risks of downloading productivity tools from unverified sources, even when delivered through mainstream advertising channels.
For enterprises, the campaign underscores the importance of enforcing strict application controls, monitoring network traffic for unusual connections, and educating employees about malvertising threats.





