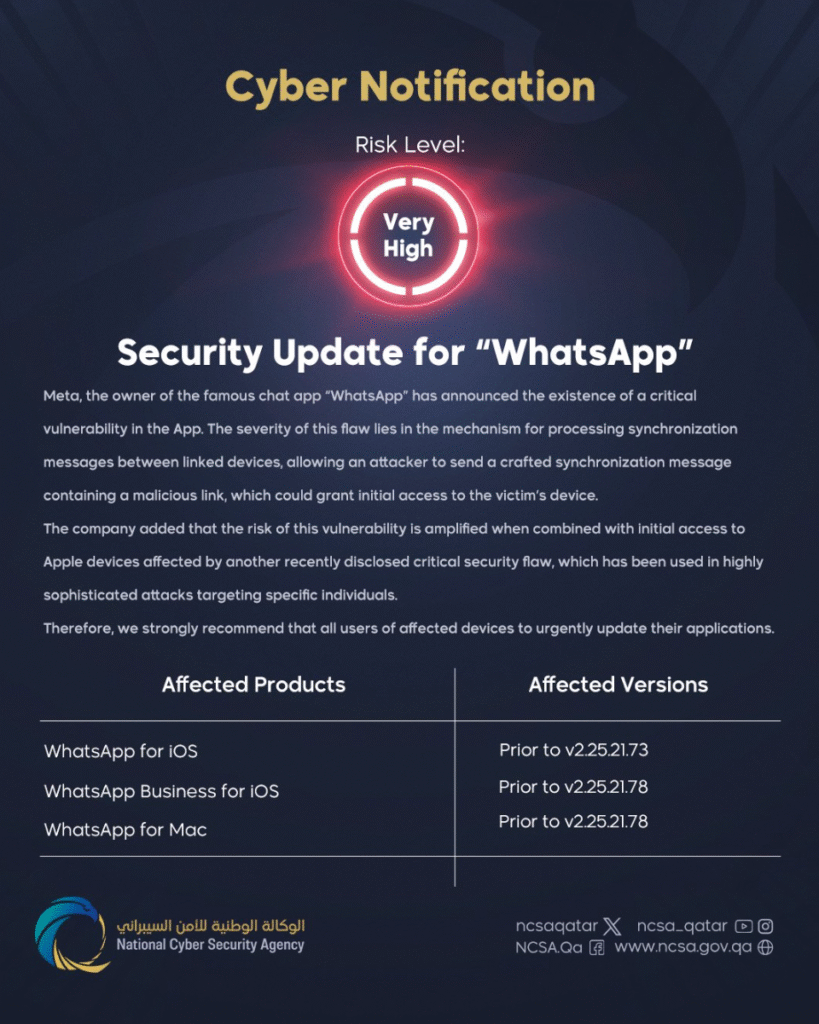
WhatsApp has patched a critical 0-day vulnerability actively exploited against iOS and macOS users. The flaw, tracked as CVE-2025-55177, enabled attackers to deploy zero-click spyware capable of stealing sensitive data without any user interaction.
Meta, WhatsApp’s parent company, confirmed that the bug was exploited in targeted attacks against “specific users” and urged all customers to update their apps immediately.
How the 0-Day Worked
According to WhatsApp’s advisory, CVE-2025-55177 was part of a chained exploit combining two separate vulnerabilities. This allowed attackers to remotely compromise iPhones and Macs running WhatsApp without requiring clicks, downloads, or other user actions.
Researchers described the flaw as a zero-click attack. Once exploited, the spyware could harvest personal files, communications, authentication tokens, and potentially escalate privileges for deeper device access.
Discovery and Exploitation
WhatsApp’s internal security team discovered the flaw while investigating suspicious activity targeting a small group of users. The company confirmed the exploit was being used in live attacks before the patch was issued.
While Meta did not attribute the campaign, experts believe the exploit resembles commercial spyware operations used by state-sponsored actors. The use of zero-click chains suggests the attackers were well-resourced and highly selective in their targeting.
(Source: x/Qatar_Tribune)
Who Was Targeted
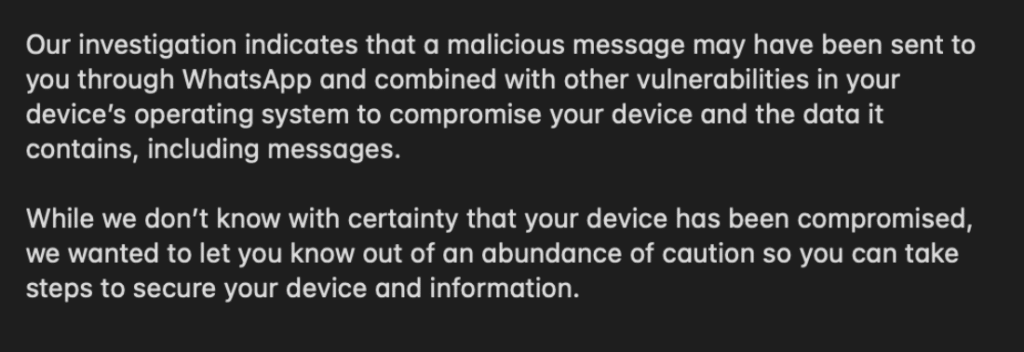
WhatsApp declined to provide details on victims but confirmed the attacks focused on iOS and macOS users. The exploit chain appears designed to bypass Apple’s security controls and compromise devices through WhatsApp’s messaging platform.
This mirrors earlier spyware cases, such as Pegasus, where attackers exploited messaging apps to silently deliver payloads. By targeting Apple devices, adversaries sought access to high-value individuals who rely on iOS and macOS for both personal and professional use.
WhatsApp’s Response
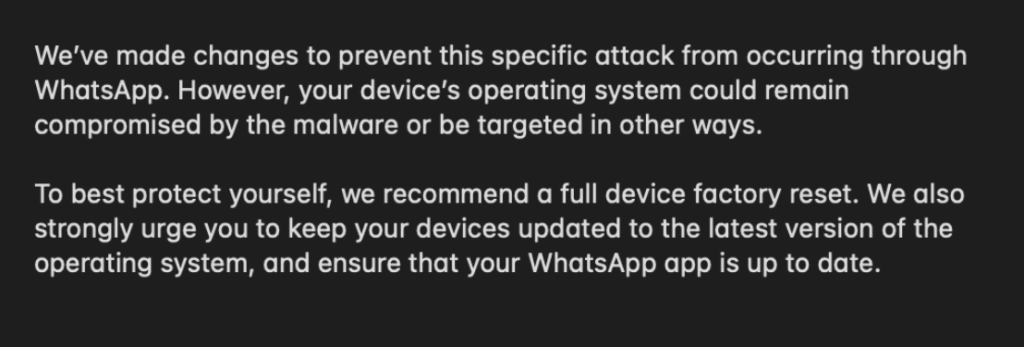
WhatsApp released patched versions of its app for both iOS and macOS, closing the vulnerabilities. In its advisory, the company stated:
“We encourage all users to update WhatsApp immediately through the App Store to ensure they are protected from this exploit.”
The company also notified regulators and is sharing technical details with the security community to aid further analysis.
(Source: x.com)
Security Community Reactions
Researchers welcomed the quick patch but stressed the severity of zero-click attacks. Unlike phishing, where user awareness plays a role, zero-click exploits leave victims with no opportunity to defend themselves.
“Anytime we see WhatsApp 0-days, especially on iOS, we have to assume this is high-end spyware work,” one analyst noted. “It reinforces how messaging apps remain prime targets for surveillance operators.”
This incident underscores the ongoing risks tied to messaging platforms. WhatsApp, used by more than two billion people globally, remains a high-value target for attackers seeking entry points into personal and enterprise ecosystems.
The WhatsApp 0-day is the latest in a series of zero-click exploits targeting Apple devices, revealing the arms race between app developers and spyware operators. For everyday users, the best defense is fast patching. For organizations, the event is another reminder that even trusted apps can be leveraged for surveillance.





