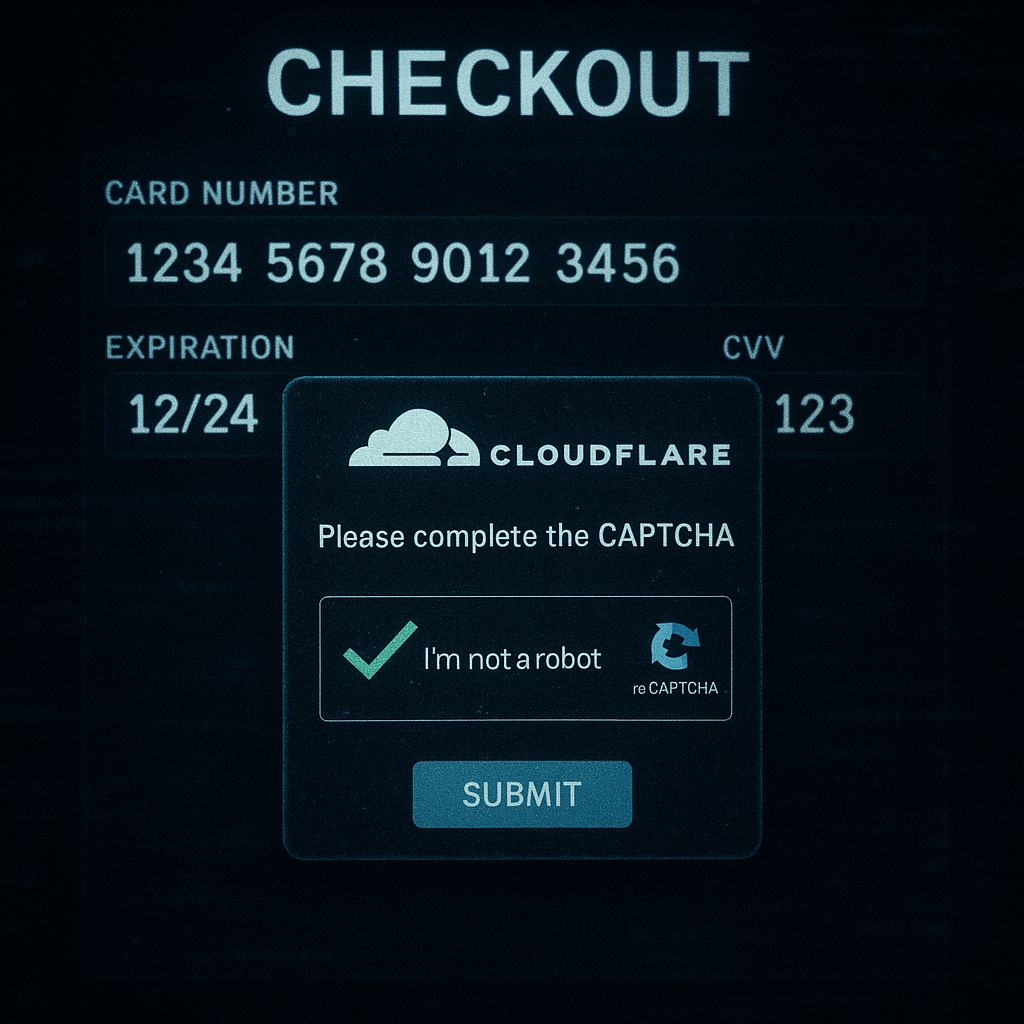
A sly WordPress malware campaign, spotted in June 2025, targets e-commerce sites by posing as Cloudflare’s verification prompt on checkout pages. Sucuri researchers warn it steals payment details, hitting online retailers hard. This article breaks down the attack, its fallout, and quick steps to secure WordPress stores.
Fake Cloudflare Trick Steals Data
This WordPress malware slips JavaScript into WooCommerce checkout pages, mimicking Cloudflare’s CAPTCHA to fool shoppers. When users click the fake prompt, it grabs credit card info and addresses, sending them to hacker-controlled servers. Sucuri notes the code’s obfuscation hides it from most scanners Sucuri.
The malware blends into site designs, making it tough to spot. It targets high-traffic checkout pages, exploiting trust in Cloudflare’s brand. Over 4,000 WordPress sites, mostly small retailers, have been hit since early 2025, with stolen data fueling dark web sales.
How Hackers Break In
Attackers exploit outdated plugins or themes, like unpatched Elementor versions, to plant the WordPress malware. WPScan lists these vulnerabilities as common entry points WPScan. Weak admin passwords or brute-force attacks also let hackers inject scripts into checkout pages.
Once inside, the malware tweaks .htaccess files to stay hidden and redirect traffic. Small retailers, often short on security expertise, are prime targets. A hacked site in Ohio lost $30,000 in fraudulent charges before noticing, showing the real-world pain of these attacks.
Damage to Stores and Shoppers
This WordPress malware drains revenue through chargebacks and fraud. GoDaddy Security predicts skimming attacks will cost e-commerce $1.2 billion in 2025, with small shops hit hardest SecurityWeek. Customers lose trust, abandoning sites after encountering fake prompts.
Breaches also risk GDPR or PCI DSS fines, which can sink smaller retailers. The 2023 Shopify skimmer attack, which mirrored this tactic, forced some stores to close. Stolen data, often sold on dark web forums, fuels identity theft and account takeovers — part of a growing 2025 credential breach crisis.
Fast Fixes for WordPress Sites
Retailers can block this WordPress malware by updating WordPress core, plugins, and themes regularly. Tools like Wordfence or a Cloudflare WAF stop malicious scripts. Strong passwords and 2FA on admin accounts are must-haves.
Scan server logs for odd activity, like script injections, and use managed hosting for extra protection. Staff training on phishing—like the recent DMV-themed scam—is crucial, as credential theft is often the first step in site compromise. Regular backups ensure quick recovery if malware strikes.
Securing the Future of Online Retail
The WordPress malware exposes gaps in the WordPress ecosystem. Developers must tighten plugin security with better code checks. A stricter vetting process for the plugin repository could help, though some argue it limits innovation. Both sides have merit, but stronger standards are urgent.
Security firms and hosting providers should share threat data to catch attacks faster. WordPress’s open-source flexibility is a strength, but only with vigilant updates. Retailers who act now can protect their stores and keep customers coming back.