LATEST ARTICLES
Dell Demo Platform Security Incident Looms After Extortion Claim
On July 22, 2025, Dell confirmed that its product demonstration platform was targeted by the World Leaks extortion gang, who claimed a Dell data breach occurred and threatened to release sensitive data. Dell swiftly responded, stating that no genuine customer or sensitive information was compromised and that the purported “stolen data” was fabricated. The incident…
Lynx Group Ransomware Attack on iBUYPOWER Signals Rising Ransomware Threats
The ransomware threats landscape escalated on July 22, 2025, when the Lynx group launched a devastating attack on gaming PC manufacturer iBUYPOWER and its sister brand HYTE. The attackers encrypted internal systems and exfiltrated sensitive data, threatening public release unless ransom demands were met. This computer ransomware incident echoes broader trends in supply-chain targeting and consumer data…
Remote Access Trojan CHAOS RAT Infiltrates Arch Linux AUR Packages
On July 21, 2025, security researchers uncovered three malicious Arch Linux AUR packages deploying the remote access trojan known as CHAOS RAT, targeting both mobile and desktop systems. These packages, disguised as legitimate tools, covertly install backdoors enabling attackers to hijack user systems remotely. This article explores the exploit’s technical mechanics, widespread impact, and effective best practices…
Retail Data Breach at Dior: Supply Chain Cyberattack Exposes US Customer Information
A retail data breach was confirmed by Dior on July 21, 2025, stemming from a supply chain cyberattack in May that impacted customers in the United States. Personal information—including names, emails, phone numbers, and order histories—was accessed without authorization. This article explores the incident’s timeline, the breach mechanics, implications for retail cybersecurity, and measures companies…
SS7 Surveillance Attack: New Exploit Tracks Phone Locations Without Consent
The SS7 surveillance attack, disclosed on July 19, 2025, involves a covert tracking method used by a surveillance vendor exploiting flaws in the Signaling System No. 7 (SS7) protocol. This exploit enables attackers to pinpoint mobile phone locations without telecom or user consent. This article details the technical mechanics of the vulnerability, its implications for mobile privacy, and…
Chrome Zero‑Day CVE‑2025‑6558: Fifth Exploit of 2025 Targets Crypto Users
The Chrome zero‑day CVE‑2025‑6558, discovered July 18, 2025, enables remote attackers to bypass Chrome’s GPU sandbox on Windows, macOS, and Linux. Malicious HTML can escape confined processes, placing crypto wallet credentials at risk. This article examines the vulnerability’s mechanics, the affected users—especially in crypto circles—and the urgency of patching. Nature of the Chrome zero‑day CVE‑2025‑6558 Vulnerability Google’s…
Node.js Vulnerability: Windows Device Name Path Traversal Exposes Credentials
The Node.js vulnerability CVE‑2025‑27210, disclosed on July 15, 2025, allows attackers to exploit Windows reserved device names (CON, PRN, AUX) to bypass path traversal protections and access sensitive files. This article unpacks the flaw, its real‑world consequences, and actionable mitigation guidance for developers and security teams. A Deep Dive into the CVE‑2025‑27210 Node.js Vulnerability On…
Cloudflare BGP Hijack: Dark Web Crypto Heist Thwarted
On July 17, 2025, a sophisticated Cloudflare BGP hijack attempt aimed to divert cryptocurrency transaction traffic to dark web servers. Though thwarted, the incident exposed vulnerabilities in internet routing that threaten blockchain security. This article breaks down the attack, its potential impact, and practical steps for crypto investors to safeguard their assets. How the Hijack…
BADBOX 2.0 Botnet: Android IoT Devices Turned into Global Fraud Hubs
A stealthy malware campaign has compromised over one million Android IoT devices, transforming them into a massive BADBOX 2.0 botnet. Uncovered in 2025, this threat lurks in devices like smart TVs and streaming boxes, enabling fraud and cyberattacks across 222 countries. Here’s how it works, its impact, and steps to secure your network. A Preinstalled…
Bitget Wallet Phishing Crisis: $6.3M Stolen in Fake Airdrop Scam
In July 2025, a vicious phishing campaign hit Bitget Wallet users, draining $6.3 million in crypto through fake airdrop scams. Attackers leveraged social engineering to steal seed phrases, exposing vulnerabilities even in non-custodial wallets. This article unpacks the Bitget phishing scam, its impact, and how investors can stay safe. Anatomy of the Fake Airdrop Attack…
National Public Data Leak: 2.9 Billion Records Fuel Identity Theft Crisis
In July 2025, a colossal National Public Data leak exposed 2.9 billion records on a dark web forum, orchestrated by the hacking group USDoD. Containing names, Social Security numbers, addresses, and more from the U.S., Canada, and UK, this breach ranks among the largest ever, threatening widespread identity theft. This article unpacks the breach, its…
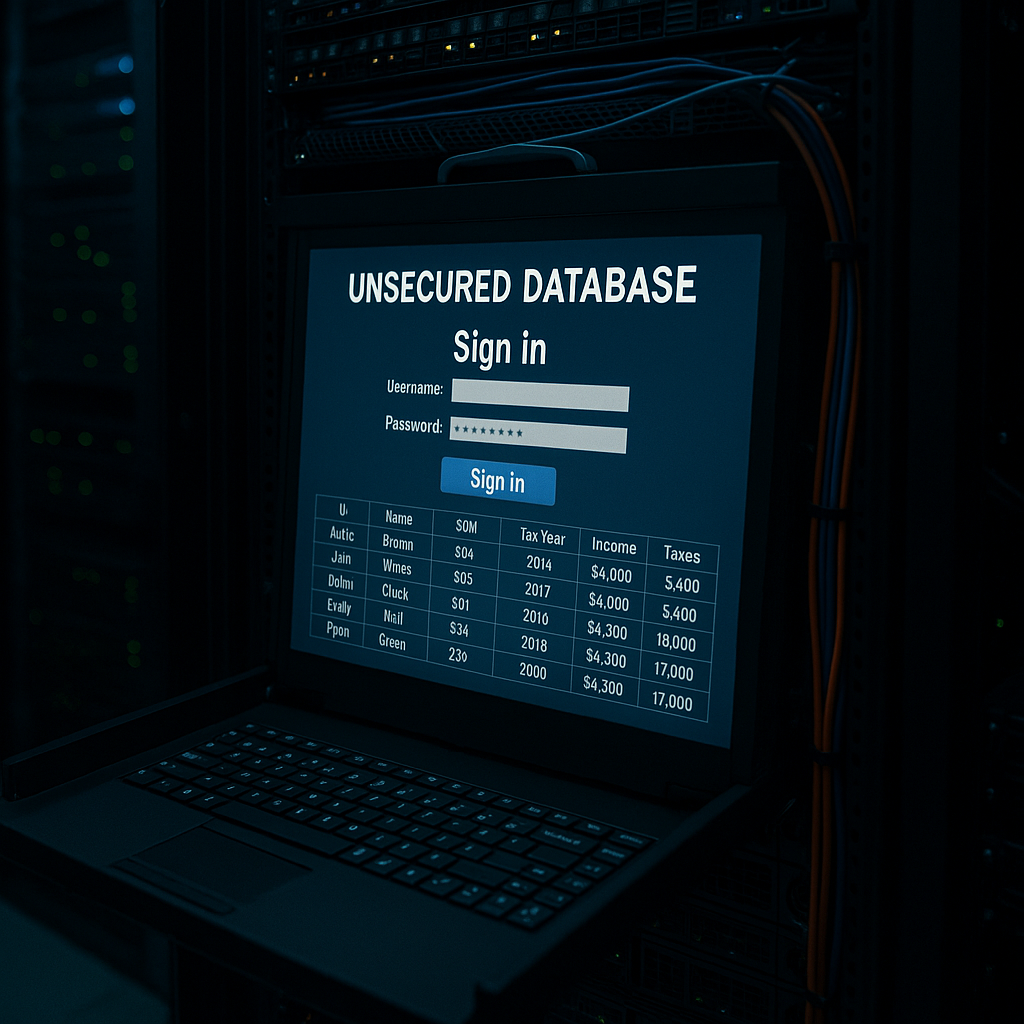
Rockerbox Tax Leak: 286GB of Client Data Exposed Online
A massive data exposure at Rockerbox, a Texas tax consultancy, has left sensitive client information vulnerable. Cybersecurity researcher Jeremiah Fowler uncovered this Rockerbox tax leak, sparking urgent concerns about identity theft. Let’s dive into how it happened, its fallout, and how to stay safe. Exposed Database: A Hacker’s Jackpot Jeremiah Fowler stumbled across a 286.9GB…