LATEST ARTICLES
Telegram’s Dark Side: Session Cookies and MFA Bypass Kits for Sale
Telegram channels have turned into bustling hubs for Telegram cybercrime, with hackers peddling stolen session cookies and MFA bypass kits to crack even two-factor-protected accounts. A 2025 report from Recorded Future shows thousands of channels offering fresh data, often tied to breaches like the 86 million AT&T leak, fueling account takeovers and fraud. Here’s what’s…
China’s LapDogs Hack: Compromised SOHO Devices Fuel Global Espionage
In 2025, a stealthy SOHO device hack campaign dubbed LapDogs turned over 1,000 small office and home office routers into a spying network for Chinese hackers. SecurityScorecard’s STRIKE team uncovered this Operational Relay Box (ORB) network, targeting industries from IT to real estate across the US, Southeast Asia, and Taiwan. Here’s how this attack works,…
Free VPNs Exposed: How Your Data Might End Up in Chinese Hands
Free VPNs promise privacy, but a 2025 study by VPNMentor revealed a troubling VPN data leak risk, with many services tied to Chinese entities harvesting US users’ data. From browsing habits to precise locations, this exposed information could fuel everything from targeted ads to state-sponsored surveillance. Here’s what’s at stake, how these leaks happen, and…
AT&T’s 86 Million Record Leak: Unraveling the Dark Web Data Dump Crisis
In June 2025, a colossal AT&T data leak rocked the cybersecurity world, with 86 million customer records surfacing on a dark web forum. Packed with names, Social Security numbers, birthdates, and addresses, this structured dataset is a goldmine for identity thieves and social engineers. Here’s a look at how this breach unfolded, why it’s a…
WordPress Malware Masquerades as Cloudflare on E-Commerce Checkout Pages
A sly WordPress malware campaign, spotted in June 2025, targets e-commerce sites by posing as Cloudflare’s verification prompt on checkout pages. Sucuri researchers warn it steals payment details, hitting online retailers hard. This article breaks down the attack, its fallout, and quick steps to secure WordPress stores. Fake Cloudflare Trick Steals Data This WordPress malware…
The Dark Web’s Role in Amplifying the 2025 Credential Breach Crisis
The dark web has become a thriving hub for cybercriminals trading stolen data from the massive 2025 credential breach, which exposed 16 billion login records. Uncovered in June 2025 by Cybernews, this unprecedented leak has fueled a surge in account takeovers, phishing scams, and identity theft, with dark web marketplaces acting as the engine behind…
Crypto Heists Surge: Analyzing the $223 Million Cetus Protocol Smart Contract Breach
In May 2025, the decentralized finance (DeFi) world was rocked by a massive smart contract breach that saw $223 million in crypto assets stolen from Cetus Protocol, a leading decentralized exchange (DEX) on the Sui blockchain. The attack, which exploited a critical vulnerability in the protocol’s liquidity pool smart contracts, underscores the growing sophistication of…
The 16 Billion Credential Leak: How Info stealer Malware is Redefining Data Breach Risks
A massive data breach exposing 16 billion login credentials has sent shockwaves through the cybersecurity world, marking one of the largest leaks in history. Discovered by researchers at Cybernews in June 2025, this colossal credential leak spans 30 datasets, compromising accounts across platforms like Google, Apple, Facebook, and even government portals. Unlike traditional breaches targeting…
How to Manage Your SEO Strategy Safely and Effectively in 2025
As search algorithms become increasingly AI-driven in 2025, website owners are scrambling to manage a secure SEO strategy through an expanding arsenal of third-party tools, external agencies, and automated platforms just to stay visible in search results. But while businesses focus obsessively on ranking factors and algorithm updates, they’re creating a dangerous blind spot—the cybersecurity…
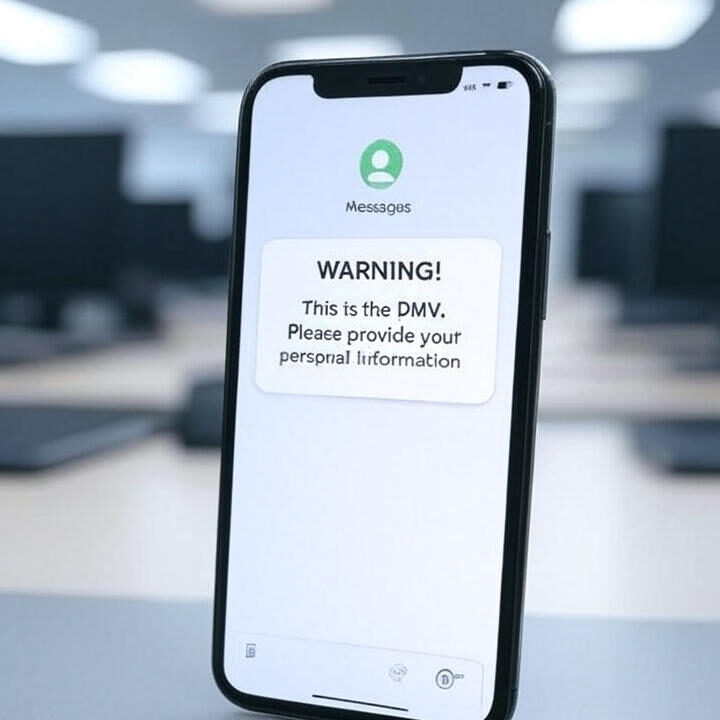
Widespread DMV Phishing Scam Hits Thousands: What You Need to Know in 2025
A sophisticated DMV phishing scam 2025 campaign is wreaking havoc across the United States, successfully deceiving thousands of drivers with convincing text messages that appear to originate from legitimate state motor vehicle departments. These fraudulent SMS attacks are harvesting everything from Social Security numbers to credit card details by exploiting Americans’ trust in official government…
Kali Linux 2025.1c Update Bug Fixes, New Hacking Tools, and Sleek Interface Upgrades
Encountering a cryptic signing key error during apt update on your Kali install? You’re not alone. The Kali Linux 2025.1c update addresses a major issue—the team lost access to their repository signing key in April 2025, breaking updates for systems worldwide. Here’s how to get your penetration testing toolkit back online and secure. The world’s…
Androxgh0st Botnet Expands: U.S. Universities Now in Crosshairs of Exploits
Recent research from CloudSEK reveals the growing sophistication of the Androxgh0st botnet, which is now targeting academic institutions such as UC San Diego. The malware uses remote code execution (RCE) vulnerabilities and web shells to infiltrate systems. Learn how this evolving threat operates — and what steps you can take to defend against it. CloudSEK’s…